The State of Smart Contracts: Many Challenges Ahead
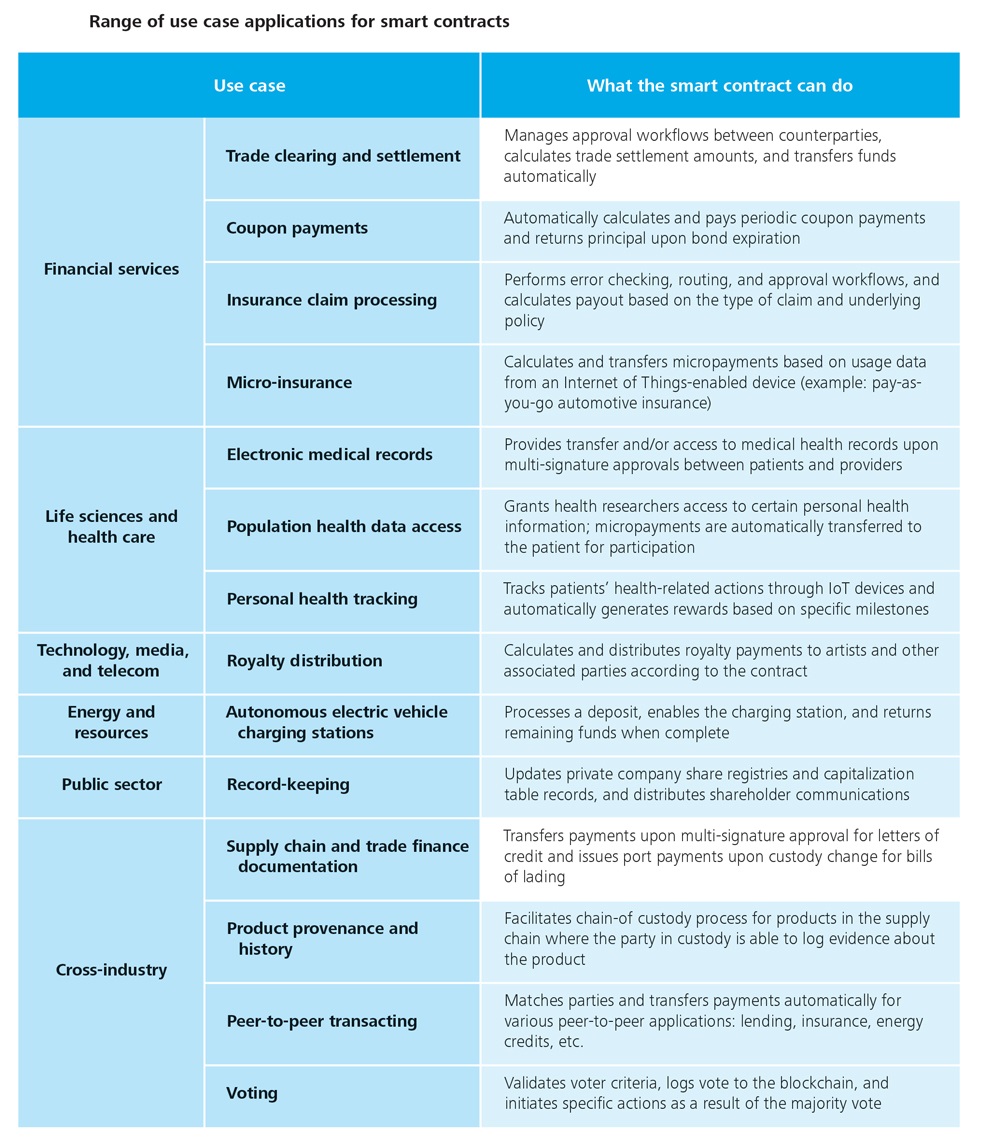
The State of Smart Contracts With blockchain technology expanding into a growing number of industries and its applications broadening by the day, organizations and individuals are to witness self-executing smart [...]











