Some of the worst data breaches have been revealed. We’ve mentioned before that with all the recent massive hacks on Sony, Microsoft, Home Depot, etc. companies are focusing more and more on the necessity of improved security measures. This recent surge of beefed up security has left some of us in the tech world wondering about some of worst hacks in history.
According to an Infographic from Information is Beautiful: “The Court Ventures hack of 2012 appears to be the biggest hack in history, in terms of number of records stolen.”
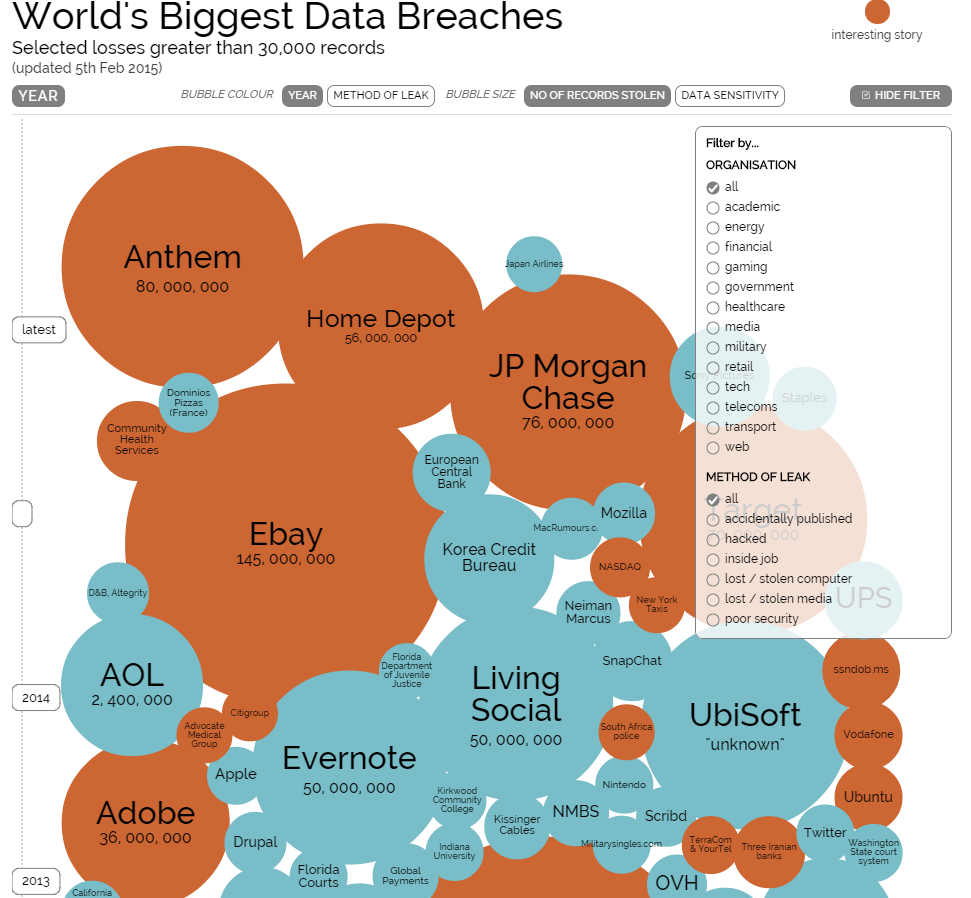
The infographic allows viewers to filter the information. Interestingly enough, some of the biggest breaches of the most sensitive data in history were inside jobs: that of the US Military and Embassy Cables in 2009 and the recent Korea Credit Bureau hack. Perhaps this data might lead to changes in the corporate screening processes for IT applicants. IT professionals are increasingly responsible for the protection of sensitive company and customer data. But what happens when an organization can’t protect itself from its own employees?
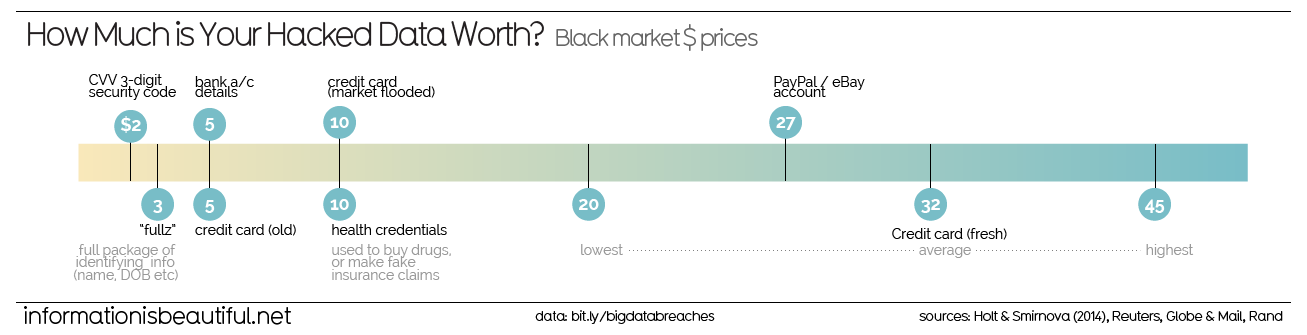
Reports from Information is Beautiful indicate: “The most valuable hacked data is that of fresh credit cards depending on their credit limit. PayPal accounts are a close second. health credentials are an unexpected third on this list, usually used to illegally buy and sell prescription drugs.”
2015 is shaping up to be the year of the cloud and improved, beefed up security. Hopefully companies can keep up with those who want to compromise sensitive customer information. Were there any hacks that they missed?
Expect the next several years to command new growth of information security tools and hosting platforms which focus on the protection of data. We are in a digital age where businesses can’t afford to have their data compromised in any fashion.
By Jason Sander





