A recent survey report conducted by the Cloud Security Alliance (CSA) revealed that sensitive data in the cloud had reached a tipping point: 64.9% of respondents (which included IT security professionals from enterprises across all industries and regions) believed that the cloud was as secure or more secure than their on-premises software. This is a watershed moment given that the single most influential item holding back cloud adoption has been the security concerns surrounding data stored in the cloud. However, in our latest Cloud Adoption & Risk Report, we found an alarming number of sensitive files that employees were storing in the cloud. This speaks both to the growing trust in the security capabilities of cloud Service Providers as well as potentially careless employees storing inappropriate data in the cloud.
According to a recent Gartner report, “through 2020, 95% of cloud security failures will be the customer’s fault.” The statistics regarding sensitive data stored in the cloud backs up this assessment. Across industries, companies have a responsibility to protect sensitive data from being hacked or accidently exposed. However, in analyzing cloud usage, we discovered that 15.8% of all documents uploaded to cloud-based file sharing applications had sensitive information.
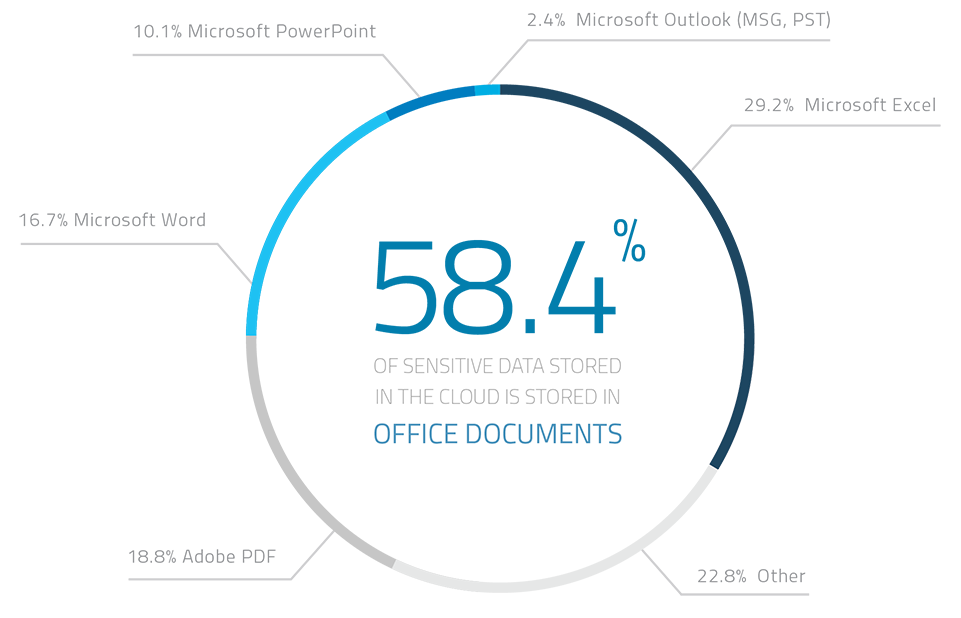
58.4% of the sensitive files were a MS office file type. 18.8% were adobe pdfs, and the remaining 22.8% were a mixtures of files types ranging from CAD diagrams to Java source code. All told, 29.2% of all files containing sensitive data were Excel files, 16.7% were MS Word files, while another 10.1% were Power Point files.
Of the 15.8% of documents that contained sensitive data, 48% were confidential files (including financial records, business plans, source code, trading algorithms, etc). 27% of documents containing sensitive were those that had Personally Identifiable Information (PII such as social security numbers, tax ID numbers, phone numbers, home addresses, etc). 15% of files containing sensitive data were one which are regulated by the Payment Card Industry Data Security Standard (PCI-DSS), while a startling 10% contained data regulated by the health Insurance Portability and Accountability Act (HIPAA-HITECH). One of the mandates of HIPAA is that if more than 500 individuals’ data gets hacked/leaked, the health care provider is required to inform the individuals as well as the press about the data loss. This can have far reaching impact both in terms of monetary fines as well as long term loss of trust and reputation.
One of the more alarming trends we uncovered was the naming convention of files that are being stored in the cloud. Cybercriminals are always looking for the types of data that can be sold in the darknet. The most valuable type of data is healthcare data, but anything from account credentials to credit numbers are common forms of data on sale in the darknet. It’s clear employees aren’t helping themselves or the organization they work for given the types of names uncovered for files stored in the cloud.
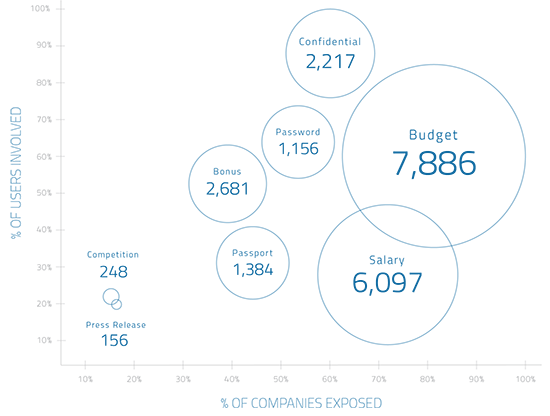
The average enterprise has 1,156 files with the word “password” in the file name. If these files gets breached, the hackers would essentially have the keys to the kingdom. A whopping 7,886 files stored in file sharing services contain the word “budget,” while 2,217 files contain the word “confidential.”
Owing to the large amounts of sensitive data being stored in the cloud, the average organization experienced 19.6 cloud-related security cases each month. These may include anything from insider threats which may be accidental or malicious, privileged user threats, stolen credentials, or attempts to exfiltrate data using the cloud.
Sadly, nearly every company (89.6%) experiences at least one threat caused by an insider each month, which lends credence to the earlier Gartner quote regarding the role the organization itself will play in cloud security breaches. At the same time, 55.6% of organizations become victims of stolen login credentials each month. The average organization is hit by an unauthorized user attempting to exploit a compromised account a total of 5.1 times each month.
If 95% of cloud security incidents are expected to be caused by an employee within an organization, then protecting data from within becomes one of the most important goals of the IT security team. However, the most difficult part of detecting insider threats is sifting through a sea of false positives to pinpoint an actual insider threat incident. As an analogy, credit card companies must detect suspicious credit card charges accurately or else the end user will be irritated by constantly having to verify their identity with the credit card company every time a “suspicious” transaction takes place. They’re mandated by their customer base to minimize false positives.
The solution that credit card companies have employed is called User Behavior Analytics (UBA), where they use Machine Learning to build a baseline for what is considered real credit card transactions. For example, they’ve realized that during the holiday seasons around Christmas time, both the amount and the frequency of credit card transactions increase for most individuals, so they use contextual clues to create the baseline normal behavior. The number of data points that is used is vast and can only be correlated using high performing computer algorithms. However, once this baseline has been established, they can accurately pick out fraudulent transactions, much like successfully finding the needle in a haystack.
Chasing false positive insider threats would be a major waste of resources, so IT security teams need to employ the same thing when attempting to detect and thwart insider threats. Every user’s cloud usage should be profiled and a baseline should be established that takes into account the location, device, time of the day, cloud service being used, and anything else visible to the security team in order to accomplish this.
By Sekhar Sarukkai





