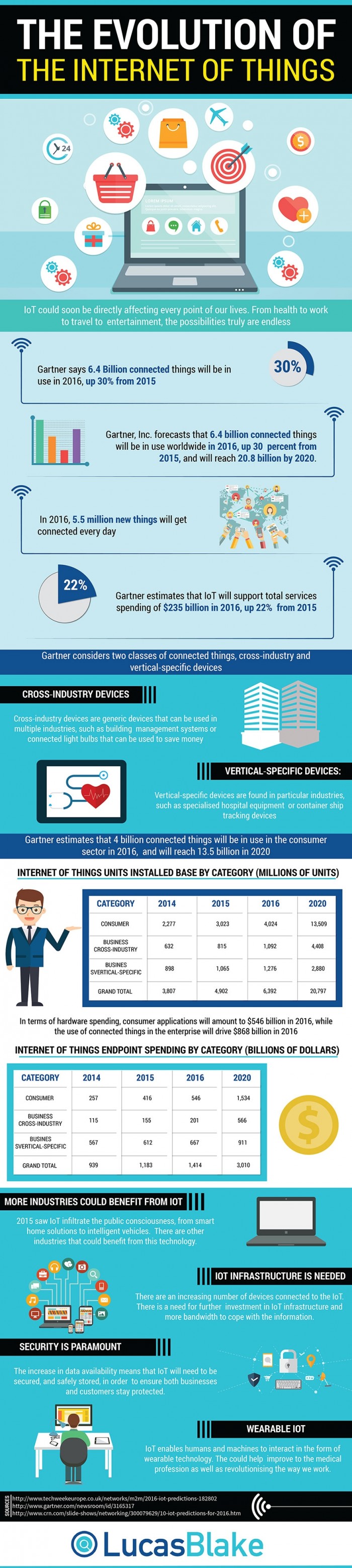
The Internet of Things, or IoT, a term devised in 1999 by British entrepreneur Kevin Ashton, represents the connection of physical devices, systems and services via the internet, and Gartner and Lucas Blake’s new infographic (below) explores the evolution of the IoT industry, investigating its potential impact across just about every aspect of our lives in the coming years. Says W. Roy Schulte, vice president and analyst at Gartner, “Uses of the IoT that were previously impractical will increasingly become practical. The IoT is relevant in virtually every industry, although not in every application. There will be no purely ‘IoT applications.’ Rather, there will be many applications that leverage the IoT in some small or large aspect of their work. As a result, business analysts and developers of information-centric processes need to have the expertise and the tools to implement IoT aspects that play a role in their systems.”
(Infographic Source: Lucas Blake)
By 2020, Gartner predicts that more than half of major new business processes and systems will incorporate some element of the internet of things, and analysts have disclosed a few more unexpected implications resulting from the Internet of Things. Until 2018, it’s predicted that 75% of IoT projects will take up to twice as long as planned, resulting in cost overruns. Unsurprisingly, more complicated and/or ambitious projects are likely to have greater scheduling overruns, and compromises made are liable to lead to weak performances, security risks and integration problems.
It’s also expected that by 2020 a black market exceeding $5 billion will exist selling fake sensors and video data. New security risks and privacy repercussions are occurring with the IoT solutions and the types of data they generate, and organizations are seeing a new kind of IT complexity which without adequate appreciation and comprehension could critically jeopardize organizations. “The IoT has enormous potential to collect continuous data about our environment,” states Ted Friedman, vice president and analyst at Gartner. “The integrity of this data will be important in making personal and business decisions… A black market for fake or corrupted sensor and video data will mean that data can be compromised or substituted with inaccurate or deliberately manipulated data. This scenario will spur the growth of privacy products and services, resulting in an extensive public discussion regarding the future of privacy, the means to protect individual privacy, and the role of technology and Government in privacy protection.”
Gartner also points to the expectation that 2020 will see an increase in IoT security costs to 20% of annual security budgets, a drastic increase from the 1% in 2015. Says Earl Perkins, research vice president at Gartner, “”Major cybersecurity vendors and service providers are already delivering roadmaps and architecture of IoT security, in anticipation of market opportunity. Small startups delivering niche IoT security in areas such as network segmentation, device-to-device authentication and simple data encryption are offering first-generation products and services, including cloud-based solutions where applicable. Large security vendors have already begun acquiring some of these IoT startups to support their early roadmaps and fill niches in their portfolios.”
By Jennifer Klostermann





