The topic of cybersecurity has become part of the boardroom agendas in the last couple of years, and not surprisingly — these days, it’s almost impossible to read news headlines without noticing yet another story about a data breach. As cybersecurity shifts from being a strictly IT issue to being a mission-critical component, BODs are also becoming more interested in what their organizations are doing to plan their incident response.
Cybersecurity professionals are smart to use the philosophy of “assumed compromise” — knowing that no matter how robust the defenses, they will be breached. Just like disaster preparedness helps in the aftermath of a major earthquake, hurricane or another natural calamity, incident-response planning helps organizations prepare in advance for the aftermath of a data breach.
In its recently released “2016 Data Breach Investigations Report,” Verizon compared being part of a infosec team to being a soldier who’s tasked to guard a hill at all costs, but without knowing who the enemy is, what it looks like, where it’s coming from and when. And to make matters worse, that soldier only has an old rifle with a few ammunition rounds.
That is certainly a fitting description of today’s cybersecurity threat landscape. Using this analogy, now imagine this soldier has extensively practiced a variety of scenarios on what an attack “may” look like, and the steps he needs to do when it does happen, regardless of how the attack plays out. This soldier still doesn’t have any more specific details about the enemy or the impending attack, but he is much better equipped for whatever unknown comes his way. That is exactly what an incident-response plan does.
You don’t have to look hard for statistics to know why you need this plan: Last year, the number of discovered zero-day Vulnerabilities more than doubled from 2014, according to the 2016 Internet Security Risk Report, newly released from Symantec. In other words, a new zero-day vulnerability popped up every week, on average. At the same time, McAfee Labs whitepaper report predicts a significant shift in the next five years “toward new threats that are more difficult to detect, including file-less attacks, exploits of remote shell and remote control protocols, encrypted infiltrations and credential theft.”
The size of the organization doesn’t matter, as bad actors don’t discriminate when they look for the lowest-hanging fruit. In its 2015 Internet Security Threat Report, Symantec found a 40 percent increase in the number of large companies targeted compared to the year before — with five of six companies becoming a target. But small businesses aren’t doing any better: In its 2015 Year-End Economic Report, the National Small Business Association found that 63 percent of the businesses fell victim of cyberattacks in the past year. Since almost 90 percent of attacks are driven by financial motivation or espionage (based on the 2016 Verizon study), if you collect and store any type of information — employee records, customer data, intellectual property etc. — you’re on the cybercriminals’ radar.
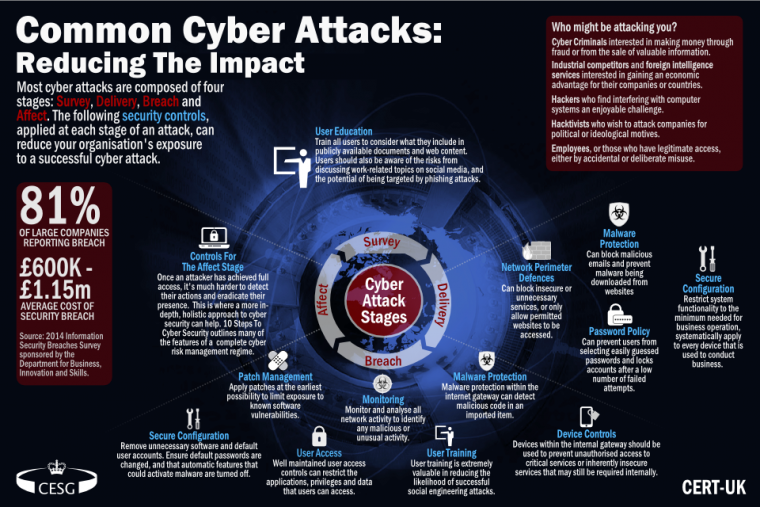
(Image Source: https://www.cert.gov.uk)
If you find yourself in the middle of a cyberattack without a plan, you’re going to scramble as fast as you can, and not just from a tactical IT standpoint to secure your information infrastructure as fast as you can. That’s just step one. If sensitive data was breached, you have a long road ahead — notifying multiple layers of stakeholders, being inundated by customer and media calls, responding to any Government inquiries, offering mitigation such as credit monitoring and potentially bracing for lawsuits. When you are in crisis mode, it’s difficult to think strategically about all these phases — it’s unlikely you’ll even know all the ramifications if you’ve never gone through an incident like this before.
That’s where incident-response planning comes in. You can give yourself ample time to consider potential scenarios and then train your employees — even taking them through actual drills and tabletop scenarios.
Look at some of the big companies’ responses to appreciate why a well-planned out response is necessary. In many of the breaches we’ve seen in the past two or three years, the post-breach actions didn’t play out as well as they should have, resulting in PR nightmares.
Target, for example, took a week to announce its data breach in 2013, in the middle of the peak shopping season, as news began to hit customers through media reports. A gridlocked customer service line and a negative social media outburst were just some of the consequences — to say nothing of the class-action suit that eventually followed, costing the company $10 million in customer settlements and another $6.75 million in legal costs. As Target struggled to contain the damage and set up an official breach-communication website, scammers acted quickly to take advantage of the chaos — sending out fake messages that claimed to be from the company.
EBay topped Target by not only taking three months to realize a breach (which is not that uncommon) but also waiting for two weeks after that to notify customers. What followed, however, was awkward for such a big player: The first announcement was posted on ebayinc.com, a little-known corporate website and when it finally made its way to the eBay ecommerce site, it only went as far as telling users to change passwords, without any explanation. Meanwhile, PayPal customers were confused because a banner posted on that website didn’t clarify whether PayPal accounts were compromised as well.
While eBay was nonchalant in social media — simply responding to a storm of complaints with a tweet saying it would take a while for all customers to receive the password-resetting email — it worked really hard to downplay the magnitude of the breach. Even going so far as refusing to give an estimate, based on its best knowledge, on the number of records potentially affected.
Anthem was also seemingly overwhelmed by the magnitude of the impact from its data breach. It took the company five days to announce a breach (which took two months to discover) and quite some time to assess the scale and communicate with stakeholders. Its original disclosure, in February 2014, put the number of records potentially stolen by hackers at 37.5 million, but then it more than doubled that estimate, 20 days later, to 78.8 million.
As an estimated 50 million consumers were yet to be informed more than a month after the breach discovery, a Senate health committee had to intervene. But that wasn’t the end of Anthem’s missteps — it took customer’s days after calling a dedicated phone line to receive a call back…
As Verizon so aptly observed in its soldier analogy, it’s challenging to defend your perimeter if you don’t know what to expect. There’s no doubt that some of the incident-response scenarios that played out in the public eye would have been different if the companies had been better prepared to not just address a breach but also plan for the right type of scale.
In eBay’s case, for example, knowing that there is no such thing as a foolproof security might have led them to an “assume compromise” philosophy. Which means having a clear understanding of where the data resides, and what risk each category of data is exposed to, based on what systems are compromised. Refusing to give an estimate a week after a breach is the first ingredient in the recipe of a PR disaster.
The second ingredient in that recipe is ignoring your own social media channels — eBay’s reaction should have been immediate in urging customers to change passwords, with a promise of more information to come as soon as details were available. One component of a communications plan in a crisis like a data breach is a handful of pre-approved templates, with ready-to-go messaging, that can be immediately disseminated to stakeholders. These messages need not alarm customers but should be transparent in stating that a potential breach was being investigated and that as a precaution customers should change passwords for their protection.
Another channel that eBay should have quickly used was its own website — and not by posting confusing, hard-to-see banners. That same collection of templates in the crisis communication plan should have had a succinct but transparent message about a potential breach and what the company was doing to secure the customer’s information.
The great thing about a well-thought-out plan is that it involves various internal and external teams, not just IT or PR but everyone from legal to risk. In the heat of the moment, it’s hard to know which teams should be activated — but with advance planning, this “all hands on deck” scenario will unfold much smoother.
Even with the increased awareness about cybersecurity risk at the BOD and C-suite level, organizations are still lagging in planning for breaches. In its an annual Global Information Security Survey, EY found that of the 1,755 executives who responded, only 43 percent had formal incident response programs for their organizations. Worse yet, only 7 percent of those that had plans integrated a comprehensive approach that included third-party vendors, law enforcement and playbooks. Much work remains to be done in this regard.
Let’s look at some basic components of a plan and rewrite the Anthem response scenario to show how things could have played out differently.
Take advantage of the built-in cybersecurity capability of vendors like Salesforce, which not only offers robust security but also provides training for your employees.
Based on this plan, in the case of the ideal Anthem response, a process would be in place to reach not only its 80 million employees and customers but also its various associates, like Blue Cross and Blue Shield, who were also compromised. Additionally, the digital media team would go all-hands-on-deck to update website and social media information, monitor social channels and respond to common questions and concerns. Plus, an external vendor would be activated temporarily to fill a 24/7, designated customer service center fielding calls related to the breach and signing up customers for credit monitoring.
This list is just a basic starting point. Incident-response plans are highly tailored to the individual organization, but best practices should be used when developing them. Not unlike a marketing plan or HR hiring manual, this plan is an important tool that helps address your organization’s success. When a breach happens, you’re likely not going to be less stressed with a plan in hand, but you will know exactly how to proceed without second-guessing your actions and missing critical steps.
By Sekhar Sarukkai





