The vision is chilling. It’s another busy day. An employee arrives and logs on to the network only to be confronted by a locked screen displaying a simple message: “Your files have been captured and encrypted. To release them, you must pay.”
Ransomware has grown recently to become one of the primary threats to companies, governments and institutions worldwide. The physical nightmare of inaccessible files pairs up with the more human nightmare of deciding whether to pay the extortionists or tough it out.
Security experts are used to seeing attacks of all types, and it comes as no surprise that ransomware attacks are becoming more frequent and more sophisticated.
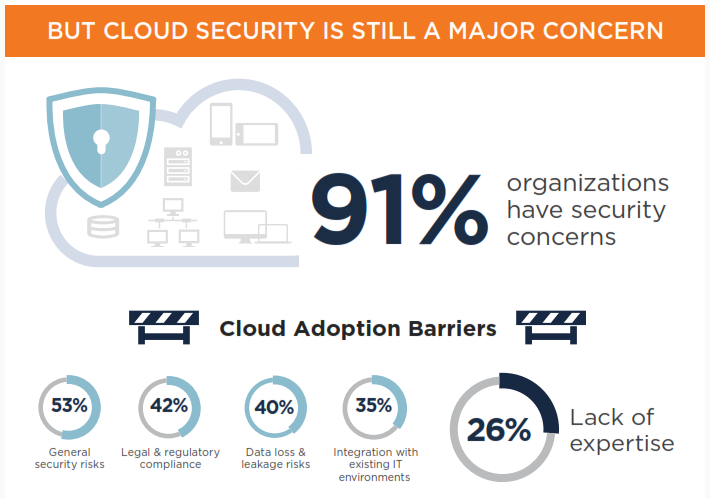
(See full (ISC)2 Infographic)
Chris Sellards, a Certified Cloud Security Professional (CCSP) working in the southwestern U.S. as a senior security architect points out that cyber threats change by the day, and that ransomware is becoming the biggest risk of 2016. Companies might start out with adequate provisions against infiltration, but as they grow, their defenses sometimes do not grow with them. He points out the example of a corporate merger or acquisition. As two companies become one, the focus may be on the day-to-day challenges of the transition. But in the background, the data that the new company now owns may be of significantly higher value than it was before. This can set the company up as a larger potential target, possibly even disproportionate to its new size.
The problem with ransomware as a security threat is that its impact can be significantly reduced through adequate backup and storage protocols. As Michael Lyman, a Boston-area CCSP states, when companies are diligent about disaster recovery, they can turn ransomware from a crisis to merely a nuisance. He says that organizations must pay attention to their disaster recovery plans. It’s a classic case of the ounce of prevention being worth more than the pound of cure. However, he points out that such diligence is not happening as frequently as it should.
As an independent consultant, Michael has been called into companies either to implement a plan or to help fix the problem once it has happened. He points out that with many young companies still in their first years of aggressive growth, the obligation to stop and make sure that all the strategic safeguards are in place is often pushed aside. “These companies,” he says, “tend to accept the risk and focus instead on performance.” He is usually called in only after the Board of Directors has asked management for a detailed risk assessment for the second time.
Adequate disaster preparations and redundancy can neutralize the danger of having unique files held hostage. It is vital that companies practice a philosophy of “untrust,” meaning that everything on the inside must remain locked up. It is not enough to simply have a strong wall around the company and its data; it must be assumed that the bad people will find their way in somehow, which means all the data on the inside must be adequately and constantly encrypted.

It is essential to also bear in mind that ransomware damage does not exist solely inside the organization. There will also be costs and damage to the company-client relationship. At the worst is the specter of leaked confidential files – the data that clients entrusted to a company – and the recrimination and litigation that will follow. But even when a ransom event is resolved, meaning files are retained and no data is stolen, there is still the damage to a company’s reputation when the questions start to fly: “How could this have happened?” and “How do we know it won’t happen again?”
As cloud and IOT technologies continue to connect with each other, businesses and business leaders must understand that they own their risk. It is appropriate for security experts to focus on the fear factor, especially when conversing with the members of the Executive, for whom the cost of adequate security often flies in the face of profitability. Eugene Grant, a CCSP based in Ontario, Canada, suggests that the best way to adequately convey the significance of a proactive security plan is to use facts to back up your presentation; facts that reveal a quantitative risk assessment as opposed to solely qualitative. In other words, bring it down to cost versus benefit.
No company is too small to be immune or invisible to the black hats. It is up to the security specialists to convey that message.
For more on the CCSP certification from (ISC)2, please visit their website. Sponsored by (ISC)2
By Steve Prentice





