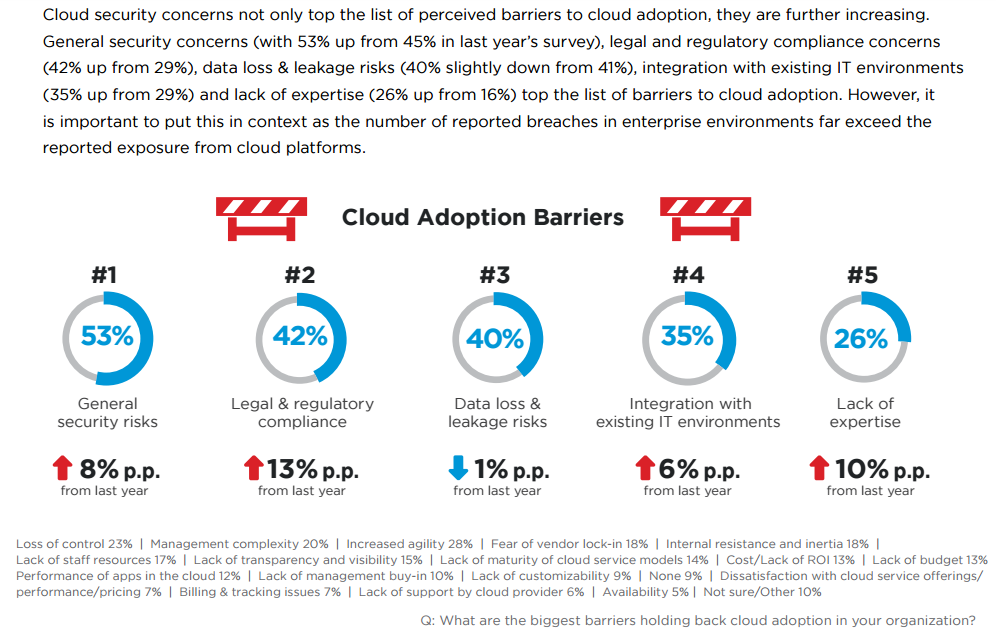
With technology at the heart of businesses today, IT systems and data are being targeted by criminals, competitors and even foreign governments. Every day, we hear about how another retailer, bank or Internet company has been hacked and private information of customers or employees stolen. Governments and oversight organizations are responding to these attacks with calls for tighter control and regulations, from the Society for Worldwide Interbank Financial Telecommunication (SWIFT) beefing up its requirements for members to new proposed regulations targeting financial institutions in the State of New York. It is no wonder that as enterprises embrace the public cloud to run their critical applications, (See image) compliance remains one of the top concerns.
Enterprises used to regard IT compliance audits and certifications, e.g., HIPAA for hospital IT systems or PCI DSS for banks and e-commerce companies, primarily from the perspective of staying on the right side of the law. But this is changing – companies across all industries are now willing to spend on IT security and compliance, not only to deal with legal requirements but also to win customer trust and ensure that they don’t make headlines for the wrong reasons.
Security and compliance in public-cloud environments are fundamentally different from private datacenter security. Old techniques and controls (e.g., connecting to physical switch TAP/SPAN ports and sniffing traffic, installing gateway firewalls at perimeters) do not work in the cloud any more. With compliance playing a key role in IT security and governance, it is important to keep a few guidelines in mind when it comes to managing public-cloud environments.
1. Start with a dose of security common sense: Common data and information security best practices lie at the heart of compliance standards such as HIPAA and PCI DSS as well as of security frameworks such as the CIS Benchmarks for Amazon Web Services (AWS). For example, compliance rulesets for cloud environments typically stipulate password policies, encryption of sensitive data and configuration of security groups. Enterprise IT and security teams would do well to incorporate these rules into their security management, irrespective of compliance requirements.
2. Remember the shared-responsibility model: Public cloud providers such as AWS follow a shared-responsibility model; they manage the security of the cloud and leave security in the cloud (environment) to the customer. These clouds have invested heavily to build security into their products and develop customer confidence. AWS has robust controls in place to maintain security and compliance with industry standards such as PCI and ISO 27001. In going from datacenters to public cloud environments, security administrators need to understand what aspects of security compliance they are responsible for in the cloud. This requires cross-functional collaboration between the operations and security teams to map the security controls in the datacenter to those in public-cloud environments.
3. Stay compliant all the time: In the software-defined world of public clouds, where a simple configuration change can expose a private database or application server to the world, there are no second chances. Enterprises are going from periodic security checks to continuous enforcement and compliance. Businesses that develop and deploy applications in clouds need to bake security and compliance checks into the development and release process. A software build that causes a security regression or does not meet the bar for compliance should not be released to a product environment. Enterprise IT needs to ensure that the tools they use for compliance monitoring and enforcement allow them to check applications for compliance before they are deployed.
4. Automate or die: Manual security and compliance processes don’t work in the dynamic, scalable world of the public cloud. When a business’ cloud environment spans hundreds or thousands of instances across accounts, regions and virtual private clouds, just the process of gathering the data required to run a compliance audit can take days or weeks, driving up the time to compliance and increasing the risk of errors. Even a team of qualified security personnel may not be able to detect Vulnerabilities and respond in a timely manner. Automation is key to survival in the public cloud. It is no wonder that Michael Coates, the trust and infosec officer of Twitter, said “Automate or die. This is the biggest thing I stick by in this day and age.” In selecting the tools to manage compliance in cloud environments, enterprise IT must regard automated data aggregation, compliance checking and enforcement of security gold standards as table stakes.
5. Don’t just find it, fix it: There is an abundance of security-monitoring products in the market today that allow administrators to find security misconfigurations and vulnerabilities but do not offer the control to fix these issues. These tools are limited in scope and utility and force enterprise IT to use a patchwork of tools to manage the security and compliance lifecycle. Businesses should pick comprehensive “find it, fix it, stay fixed” platforms that do not stop at identifying issues with the environment but offer the tools required to fix them and put safeguards and controls in place to ensure that security best practices are enforced.
Public clouds are transforming the world of enterprise IT by offering unprecedented agility and a pay-as-you-grow operational model. Clouds are also changing the rules of the game for IT security and compliance management by offering new controls and capabilities. The tools and processes that served IT well in datacenter environments will not work in the public cloud. It is time for security and compliance to be transformed as well.
By Suda Srinivasan





