Spies and thieves often do their best work by hiding in plain sight. No one suspects the person sipping coffee at the table across from you in the coffee shop – the one who happens to be reading your computer through the unsecured Wi-Fi. No one ever thinks that the PIN they enter at the ATM or debit card terminal is being watched by someone a few feet away. Few people consider the danger of including their real birthdate when opening a membership online. And certainly no one ever suspects the printer of anything at all except occasionally needing paper.
But these are all examples of how we use technology daily to solve our immediate concerns without additional thought. Life would be very hard without Wi-Fi, ATMs and printers. Their roles are as quiet, subservient support technologies. They are the discreet butlers of our digital lives. No one ever suspects the butler.
It is for that reason – that lack of diligence – that printers have become the gaping hole in the wall of cybersecurity. Companies spend billions of dollars annually seeking to protect networks and ensure that computers are safe and virus free. But few people pay attention to the silent peripherals.
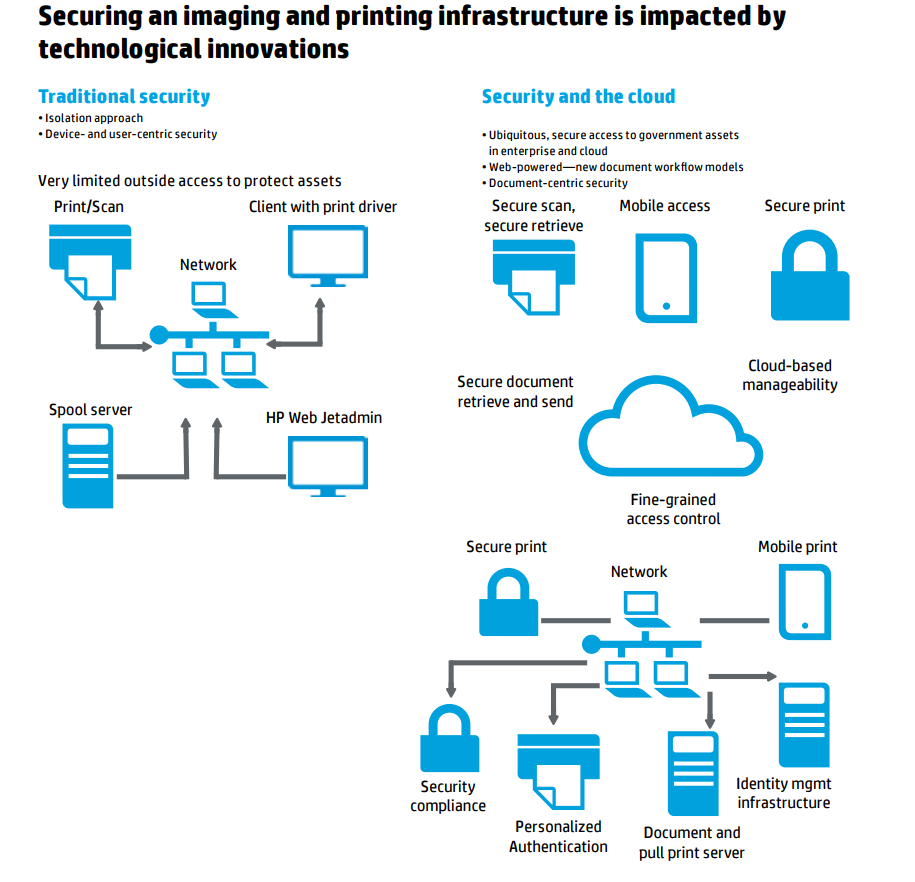
Decision makers seldom hear about hacks through printers. To the average, honest working person, they are simply output devices. But to the wearers of the black hats, they are willing and compliant access points, not only to a company’s existence, but beyond, to everything that company is connected to, out there on the internet.
The most infamous DDoS attack in recent memory happened on October 21, 2016, when a brand of malware called Mirai brought Netflix, Twitter, Amazon and others to a crawl. Experts believe this Malware made its entrance through an unprotected Internet of Things (IoT) device like a printer, a router or a camera. These are devices that are seldom protected by vigorous passcodes and anti-hacking tools. They’re just simple devices after all.
But this is where innocence and naiveté have no place. The belief that such devices are low risk, having little value to hackers, is fatally incorrect. To remain unaware of just how a sophisticated hacker can use an unsecured printer to access the network is precisely the type of thinking that can bring companies down. To forget just what lives inside a printer – images of documents, user credentials – is downright dangerous.
Every device, no matter how innocent looking, must be included inside a rigorous and regular security audit, must be monitored regularly, and must be brought up to speed in terms of security software. If a device can communicate, if it has a computer inside, no matter how small, it can be compromised.
The people who use these devices must be trained in the same type of hygiene that they currently (hopefully) apply to their network passwords and laptops. There must be a mechanism to enforce policies.
Printer security does not end with shoring up the software. Companies must also consider the people on the inside who are using these devices daily.
The key message is that printers play a fundamental role in business life, both at the Workplace and in peoples’ homes. They are communications devices armed with computing power, and if left unsecured, they become dangerous. Secure printers must be equipped with features like secure whitelisting, run-time intrusion detection, automated compliance, usage certificates, and even a “golden BIOS copy” to revert to, should a compromise be detected.
As more and more devices connect to the global network, they increase convenience, but at a cost of substantially weakened security. A printer that is not secure should be turned off and physically disconnected, since the bad guys are getting much better at hiding in plain sight.
For more information on printer security, visit HP’s Secure printing page and check out the webinar. To do a quick self analysis of your printers, visit HP’s analysis page here.
This post is brought to you by HP and IDG. The views and opinions expressed herein are those of the author(s) and do not necessarily represent the views and opinions of HP.
By Steve Prentice





