Cybersecurity today has become far too reactive. The constant innovation of hackers has meant that defenses are made up of a patchwork of web application firewalls, end-point protection, data-loss protection, and more. This can lead to a combination of end-point protections that don’t function well as a whole.

John Davis, CSO of Palo Alto Networks’ federal division, suggested that too many firms have given in to the hackers by resigning themselves to this reactionary approach. They accept that the hackers will access their network and therefore focus their time and resources on minimizing the damage. “Some of our industry has given up on the ability to prevent and is focused primarily on detection and response, which means, with a mindset like that, it means you’re always involved in cleaning up aisle nine, as some people like to say.”
Instead, he urges companies to adopt a more forward-thinking approach, an enterprise-wide culture that starts from the top. “Look at the headlines—breach after breach after breach. And so, these issues today are becoming CEO and boardroom issues. They are not dealt with strictly in the environment of the IT world.”
A recent Economist Intelligence Unit (EIU) survey (sponsored by VMWare) found that nearly half of C-suite respondents felt that cybersecurity measures were a hindrance to critical functions, delayed product launches, and stifled innovation. Given that average costs for each lost or stolen record containing sensitive and confidential data hit $158 this year, it seems counterintuitive to adopt a reactionary security policy that drains time, money, and resources.
Jim Payne at Ring Central argues that this culture leads management to becoming apathetic and resentful of cybersecurity spending, fuelling a reactive culture rather than a proactive one. By allocating your cybersecurity budget to plan ahead, you allow IT executives to prioritize against the greatest threats and deploy next generation defenses before potential breaches are exposed.
“Effective planning and prioritization also gives IT a fighting chance of deploying flexible, adaptive solutions versus asking management to allocate budget for cybersecurity that will be outmoded by the time it is deployed,” says Payne.
Another study performed by the EIU found that a proactive, enterprise-wide cybersecurity strategy could reduce the growth of cyber attacks and breaches by 53% over comparable firms.
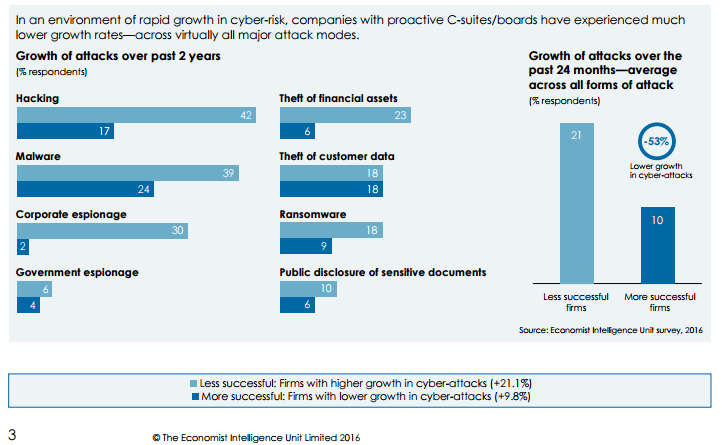
Board engagement is key to this strategy succeeding: only the C-suite has the influence and resources to effect a truly efficient and effective transformation of cybersecurity policy. Jeffrey Ritter, author of Achieving Digital Trust, states that, “Boards become actively involved in security when they realize that security drives revenues and customer loyalty… If partners or customers are not confident about how secure your business is, they will decide to not do business with you.”
As well as changing policy from within, there are measures that can be taken to find bugs that you miss, such as “bug bounty” programs—offering rewards to ethical hackers for discovering flaws before they can be taken advantage of.
This isn’t a change that can be made overnight. It takes time and effort to develop good security governance across an entire organization. However, with a forward-thinking and education-driven security policy, you can expect to see significant savings and a reduction in cybersecurity breaches. It is critical that this culture is adopted and driven from the top down, or the reactive and unreliable approach may start to creep back in.
Sponsored series courtesy of Ring Central
By Josh Hamilton





