In an ideal scenario, the people at the highest levels of an organization would be the most likely to abide by data protection policies. Then, their positive behavior could set an excellent example for everyone at the lower tiers of the company.
Unfortunately, one survey revealed this isn’t the case most of the time. The results showed that 78% of directors intentionally shared data in ways that didn’t align with company policies. In contrast, the same was true for only 10% of clerical workers.
What was the most likely situation when directors behaved this way? The research showed that 68% of them did so by taking information with them to new jobs. The overall average of people breaking policy was only 46%, illuminating that directors represent the group most likely to misuse data.
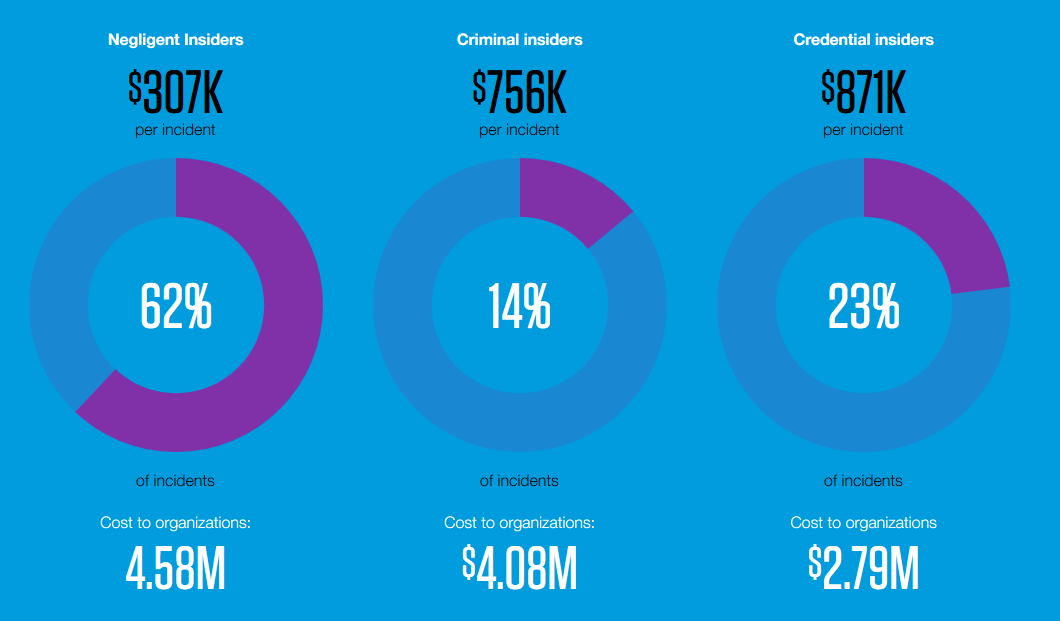
An insider breach occurs when someone who works at a company is directly responsible for causing it. Recent research indicates that insider breach costs are on the rise. Findings pinpointed a 31% increase in insider breach costs, with the average expenses totaling $11.45 million. Therefore, it makes sense that enterprises would want to do anything possible to protect data.
Numerous companies offer tools that aim to make breaches less likely or make information less usable to hackers who might seize it. However, research suggests they are not at a point of widespread usage. Only 48% of respondents use email encryption, and 47% of those polled provide workers with secure collaboration tools.
Some companies have no choice but to implement better breach prevention methods. The U.S. Department of Defense (DoD) recently introduced a framework that outlines various levels of cybersecurity maturity. All parties doing business with the DoD must meet the requirements within the first level. Regardless of whether a company receives contract work, it should prioritize cybersecurity before it’s too late, and representatives discover data breach evidence.
Perhaps a positive finding is that 58% of respondents said they found out about insider breaches through workers. The study did not detail which methods companies use to facilitate such reports.
However, employees speaking up is a good thing. In addition to implementing a data breach policy that expects employees to mention what they know, companies must make it straightforward for workers to share information.

When many people think of insider breaches, images of disgruntled employees seeking revenge likely come to mind. However, these incidents often occur when outside parties successfully trick employees into giving up valuable or confidential information. In fact, 41% of employees said they caused a breach by responding to a phishing email. Unfortunately, the research said only half of companies polled use antivirus software to screen for such content.
While phishing was the top cause of unintentional data breaches, sending emails to the wrong recipients was the next most likely culprit, cited by 31% of people. Some companies aim to address the problem with an “undo send” feature. Yet these aren’t perfect, especially if a person has to use that option within seconds.
Another worrying finding spotlighted an apparent data ownership discrepancy. More specifically, 29% of employees admitted to intentionally sharing information in ways that did not align with their company’s policy in the past year. Then, as pointed out earlier, 46% of overall employees did so when moving to a new job. However, 26% said they took risks when sharing data due to lacking the proper security tools.
What can and should IT professionals do given these findings? First, they must not assume that people at the highest levels of an organization do everything right to keep data safe. Also, it’s smart for them to invest in tools that can discover breach Vulnerabilities and allow remediation before problems crop up.
Upcoming employee training sessions should teach workers how to avoid scams, and company executives should assess their budgets to consider if there is money available to invest in software that looks for phishing attempts.
A best practice is to have a data breach policy that tells workers what to do if they know of or suspect an insider data breach. The plan should also explain information ownership, including what happens if an employee leaves.
Preventing an insider data breach is not easy. However, the cost and risk involved make it imperative.
By Kayla Matthews





