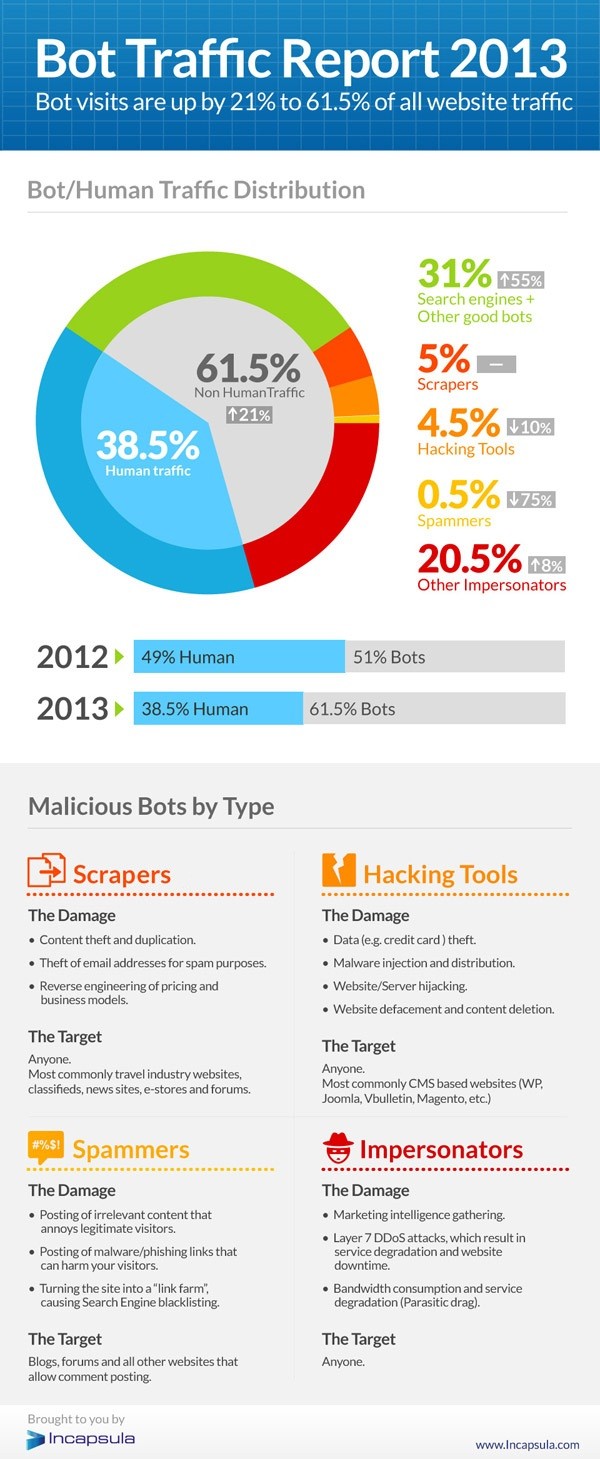
Cybercrime Transformed By Modern Computing and New Digital Age
Cybercrime Transformed By Modern Computing We stand on the edge of the digital age, where technology moves quickly, and our lives have been transformed by modern computing. Digitization has resulted [...]