A ‘bot’, short for ‘web robot’, is a small software application that can run automated tasks over the internet. Their primary function is to fetch script and analyse web server information at a considerably faster rate than a human could achieve.
Unfortunately, cyber-criminals have been quick to take advantage of the technology. ‘Bad Bots’ are now considered to be one of the most sophisticated types of crime-ware facing the internet today.
Founded in 2011, Distil Networks is the leading public and private cloud security provider for blocking malicious bots and other automated computer programs from attacking a website. They have just released a new report titled ‘The Bad Bot Landscape’. The report analyses their own extensive database to reveal key information about the sources and uses of bad bots in 2014.
CloudTweaks takes a look at some of their findings…
Historically it has been presumed that the vast majority of bad bots originate in three places – Russia, China, and India. The assumption has always been that countries with a below-average level of internet security are a perfect location from which cyber-criminals could base their activities.
Interestingly, Distil’s report disproves the theory, instead finding that these countries only occupy the fifth, eighth, and seventeenth spots on the list respectively. Remarkably, the top four countries on the list are all places that are considered to have excellent levels of internet security and cyber-criminal defence – specifically the US, the UK, Germany and the Netherlands.
Distil point out that the main consequence of this finding is that owners of websites should not try to block traffic based on its country of origin. It is an ineffective method that bot owners will easily be able to circumnavigate.
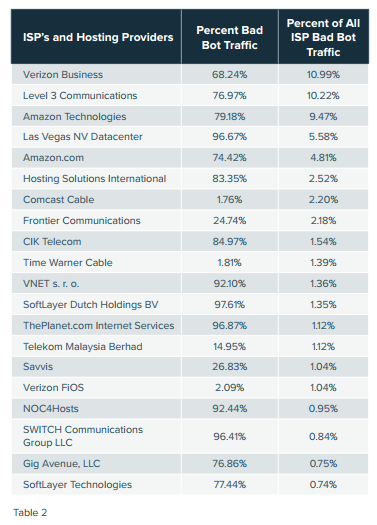
Yesterday we looked at cloud-based fraud, and one of our conclusions was that hosting could be purchased cheaply and anonymously by criminals by using a stolen credit card. For this same reason, hosting providers are also highly popular amongst bot creators. The knock-on effect of this is that ISPs that provide bandwidth to hosting providers are the origin a large percentage of bad bot traffic.
In their report, Distil noted 1,132 organisations that could be classified as either an ISP or hosting provider which have at least 70 percent of their entire traffic volume consumed by bad bots. Some companies, such as SWITCH communications Group and SoftLayer Dutch Holdings, are close to 100 percent – clocking in at worrying 96.41 percent and 97.61 percent respectively.
They conclude that the commonly held belief that blocking the world’s largest hosting sites, such as Amazon Web Services, will protect against the majority of bad bots is actually a fallacy. Only 14.28 percent of the world’s bad bot traffic originates from Amazon, meaning this methodology would still leave you exposed to 85 percent of bad bot traffic.
Distil claim that even if an organisation blocks the worst offending ISPs and hosting providers, they would still be exposed to 40 percent of the world’s bad bots – that’s roughly 2.1 billion malicious codes.
What steps do you take to protect yourself from bad bots? Have you experienced a cyber-criminal attack in your organisation? Let us know in the comments below.
By Daniel Price





