(Updated August 11th, 2020)
IBM, Amazon, Google, Yahoo, Microsoft – and the list goes on. All these leading IT enterprises have been affected by Cross-Site Scripting (XSS) attacks in the past. Cross-Site Scripting ranks third in the list of top-10 web application vulnerabilities listed by the Open Web Application Security Project (OWASP) – a worldwide non-profit community focused on improving the security of web applications.
The history of ‘Cross-Site Scripting’ vulnerability dates back to the middle of 90’s decade. It was Microsoft who first introduced the term to refer to a security flaw specific to ASP.NET environment that made dynamically generated HTML pages vulnerable to malicious scripting attacks.
Cross Site Scripting (XSS) can be defined as the process of inserting malicious code to a web environment to compromise the security of the system. It is a client-side attack where an attacker injects specifically coded scripts through a web browser program. The code appears to have originated from a trusted source and the browser executes the script – resulting in the attacker gaining access to the system. A host of scripting languages, including JavaScript, VBScript, Flash or HTML/CSS, can be used to launch XSS attacks on vulnerable web-based systems and applications.
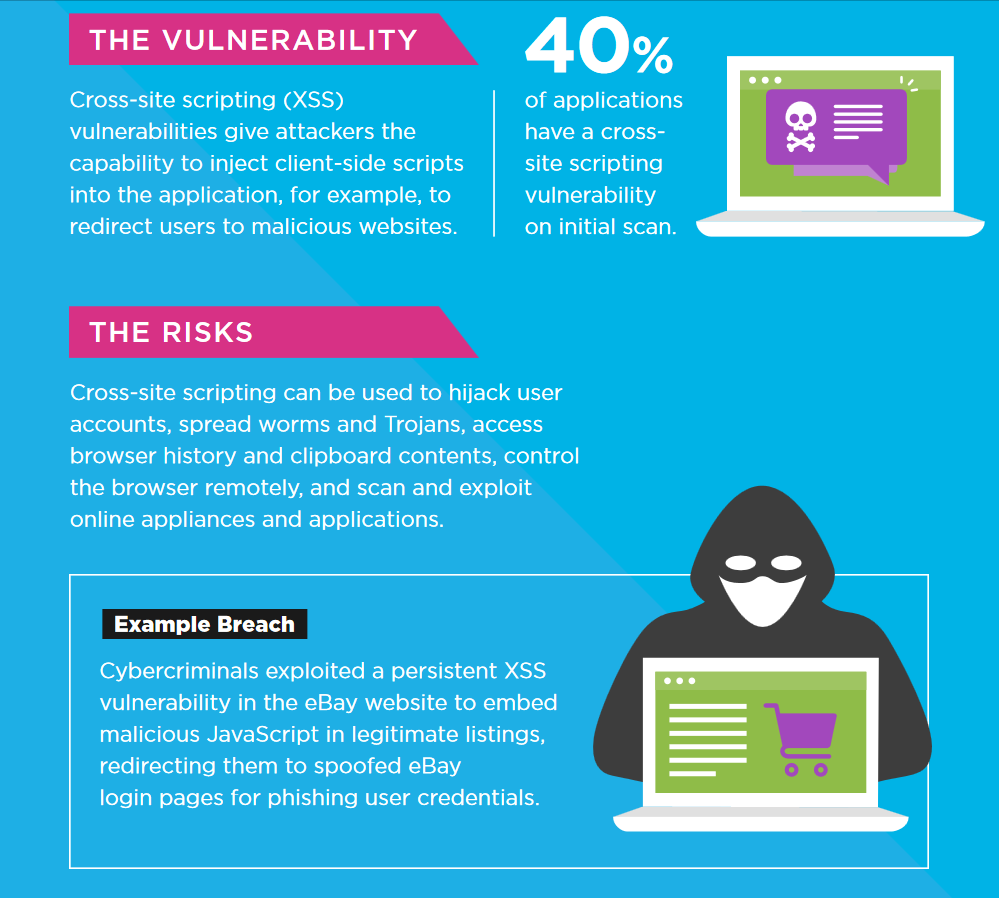
(Infographic source: Veracode)
Cross-Site Scripting is a web-based vulnerability that can affect all Big Data Projects that use web-based systems, tools or applications. As most of the data analytics and business intelligence applications are interactive web-based solutions (that accept and execute user inputs), there is always the possibility of cross-site scripting attacks if the inputs are executed without validation.
Web-based applications continue to fall prey to Cross-Site Scripting attacks as they are mostly interactive. That means, they need to accept inputs from the users and return the output based on the inputs received. This gives an attacker the opportunity to manipulate the inputs and insert malicious scripts or commands through normal input channels.
Cross-Site Scripting – Behind the Scene:
Cross-Site Scripting attacks mainly exploit authentication bugs in the application layer to insert scripts that are executable on the client side. Typically the attack vector is based on brute force to hijack legitimate user sessions. Such attacks bypass access control policies to help the attacker take the identity of a valid user. Cross-site scripting has the ability to elevate the hacker in gaining administrative control on the application server – thus compromising the security of the entire environment.
The risk of XSS is not limited to Big Data applications alone. All types of web-based solutions are vulnerable to cross-site scripting attacks. By injecting malicious executable scripts into the application layer, a hacker can gain control of underlying databases, user credentials and other sensitive information that are maintained by the application. Information gathered from the initial attack can subsequently be utilized for conducting more sophisticated hacking attempts to compromise the security of the entire project.
Contextual Input Encoding (Escaping) Techniques:
Escaping techniques, if implemented correctly, can significantly alleviate the prospect of XSS attacks. It is a form of contextual input encoding where the web browser is informed to treat specific strings of code as plain text characters.
In case an attacker manages to insert an executable script as an input to the application, the browser would first validate the input before executing. If it matches with the specific strings that are supposed to be interpreted as plain text, it would terminate the session without executing the script.
HTML, CSS, JavaScript – all have their own set of escaping libraries. Instead of rolling out your own escaping codes, it is better to make use of a reputable escaping library.
Vulnerability Scanner:
Quite a few reputed anti-virus software manufacturers have come up with vulnerability scanner suites that can detect possible XSS attack areas. You should seriously consider getting one for your project. The scanner crawls the entire set-up, consolidates all the findings and lists down the weak areas which are susceptible to cross-site scripting attacks.
Penetration Testing:
Another effective measure to identify XSS vulnerability is penetration testing. Find out the possible gateways from where an attacker could gain entry to the application and try from your end to exploit those vulnerable areas. If you are successful in breaking into the system, then you need to investigate the issue further to find the root cause. Once the root cause gets identified, you can engage your developers to come up with a preventive measure.
Browser Security Features:
All major web browser programs have a built-in security feature – Response Header – that can be used to combat XSS attacks. You could make use of Content-Security-Policy header to specify how the browser would deal with script tags. You can enable execution of scripts from specific domains, while block this functionality for other domains. This technique is also known as whitelisting.
By Jack Danielson





