If you’re an average consumer, your concerns about the Internet Cloud systems should justifiably stem from the threat of the Unknown: is your data private? Is it secure? Do you own it, or does the cloud service provider? Being a marketer, however, means that your concerns will extend far beyond just these commonplace worries. Why? It’s because, as the old adage goes, with great power comes great responsibility.
Let’s take on the issue of cloud potential before delving deeper into this. Today, the cloud has a reach that we couldn’t have foreseen in, say, 2009. The Oslo metro railway system, for Instance, relies entirely on cloud-based systems to analyze its conditions. IFTTT buttons send out company notes and emails to persons concerned without any manual initiatives involved in the process.
GoogleDrive, OneDrive, Rackspace hold thousands of sensitive data and information. Banks have secure servers online with the ability to assess risks and withhold user information. Naturally, the cloud is like a giant disaster waiting to happen if used the wrong way. As a marketer, therefore, you might not feel too concerned: until you consider what is in it for you. Most marketers’ concerns should ideally stem FROM the knowledge of the kind and amount of data online, rather than a LACK of it. It’s easy to feel that you don’t need to worry about exploitation of information, sensitive storage and handling, but that’s wrong. Consumers require a safe and protected space, and your task is to give it to them.
Ten years ago, data privacy would have been no big deal for people. But with the kind of Data leaks we’ve seen in the past two-three years: NSA-Snowden, WikiLeaks, Ashley Madison, Target, people are a lot more conscious of their data.
Let’s see how the consumer feels about online marketing: if you, as a marketer, require data to market to the right demographic, you may find yourself without potential consumers simply because they don’t trust you enough to upload their data to the cloud. After all, the cloud can sometimes feel like a bit of a black-hole: no consumer ever knows what’s in there, and how much stuff is actually known about them. Naturally, everyone is concerned over protecting their identity, financial and personal information. This can be a huge problem if you’re a marketer: you want to track customers to offer them personalized services, you want to expand your relationship with them and engage them more, but you simply can’t get the info you need for it.
See what we’re getting at? Even IoT (Internet of Things), one of the most innovative new technologies that are totally dependent on the cloud, falls flat on its face if consumers can’t get the kind of security they require.
There are several reasons why the cloud is such a big part of our everyday life now. From storage solutions to online backups, from home automation to augmented computation, from finance to grocery purchases, everything depends on the cloud to work. After all, we are too impatient to wait while a server retrieves info, we just want everything quickly, and that’s where the cloud comes in.
Whether you’re a consumer or a marketer, you need remote capabilities, and fast, right? But stop, what happens to the Steam user who stops using Steam because he can’t trust the service to protect his financial and personal info? Then again, what happens if a banker suddenly decides to steal all the account information for his investors, and all their money, just because it was all safely uploaded to the cloud?
True, there are better encryption systems these days, but that does not mitigate the risks in the slightest. In 2015, there were about 411 known breaches of data, on top of the 761 from 2014 which leaked 85.6 million records. As per the Identity Theft Resource Center, 40 of past year’s breaches were in the banking and finance sectors alone: with hacks conducted at Citibank, TD Bank, BB&T, and Virginia Credit Union among some of the sufferers.
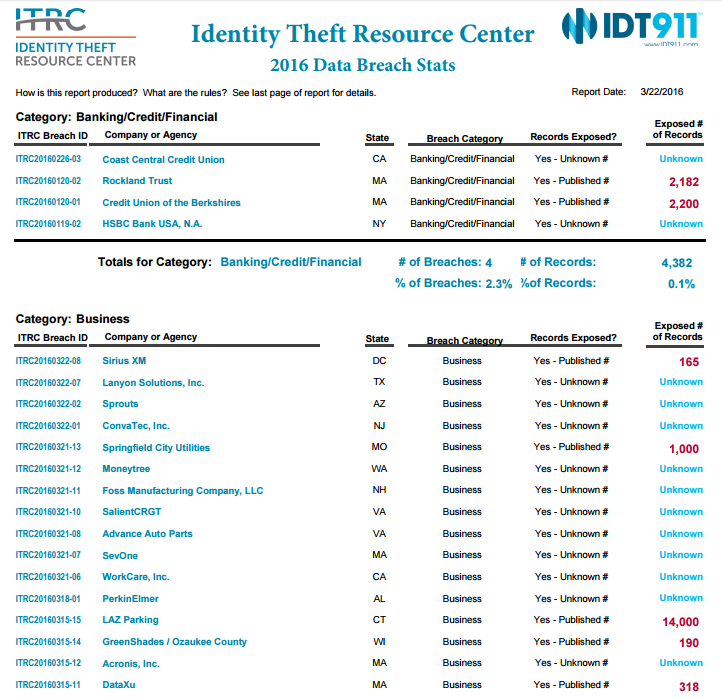
So if you are, say, a marketer for one of those banks, you would have a tough job convincing people to bank with you online, wouldn’t you?
The good news is that there’s plenty to be done for fixing privacy concerns. To meet the kind of privacy needs required, you should ensure encryption of all data. The easiest way is to choose a storage service provider who uses layered encryption. When seeking information, over-reliance on Facebook and Social Media logins can kill customer trust, so you should make sure you’re not invading into personal territory in an intrusive manner.
After all, asking for information should never be a trap: give your customers a custom-user experience by allowing them a) freedom to refrain from answering, b) information on what you’ll do to their data, c) agency to decide what is best for them, and d) security. As long as you maintain a privacy policy page which clearly states the cloud policies and security methods you’ve taken, making sure that your customers are aware of what they are signing on for, you should have little to worry about.
By Mauricio Prinzlau





