The zero trust model is becoming more commonplace in security. It’s based on the realization that threats exist inside and outside of a network.
Limiting those requires verifying a person’s permission to access something during every request they make. Here are six reasons why more companies decide that zero trust is the right approach for them to take.
One of the principle goals in traditional security models was to keep an organization’s perimeter secure. Then, a firm could feel confident that anything within it was safe. However, the digital transformations that many companies have gone through mean that the old way of doing things is no longer sufficient.
Things like Internet of Things (IoT) devices, employees working while traveling and a greater reliance on third-party providers can all make threats go up. Companies cannot assume that threat-free environments exist, and they must understand that it’s time for a new security approach. In the same ways that businesses have adjusted their operations due to digitization, they must realize that the shift necessitates an updated security model.
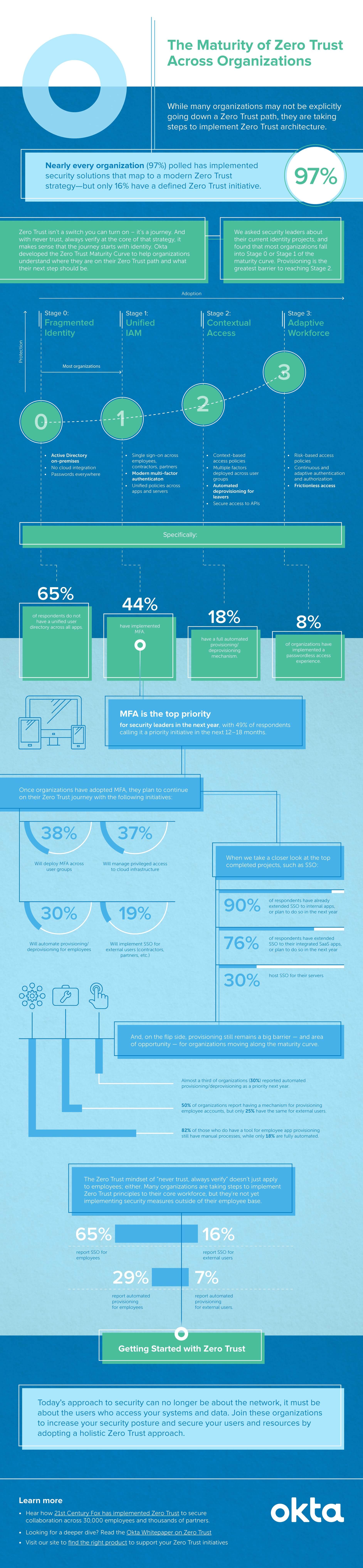
(Infographic Source: Okta)
Instead of focusing on what’s inside an organization’s perimeter, zero trust emphasizes identity verification. That means no matter a person wants to access data that’s on-premise or in the cloud, they can do it as long as the system is satisfied that they have the privileges needed to see the information.
Similarly, zero trust applies to people trying to access data on a given device, and the security framework does not require those individuals to be in a particular place to have their identities verified. Companies that frequently hire remote workers often conclude that the zero trust model makes sense due to the number of devices that a person could use to access corporate data around the globe.
In today’s society, mobile apps and portable devices make it convenient to work from anywhere. Zero trust ensures they can do that without eroding a businesses’ security standards.
Another reason why companies are increasingly adopting zero trust is that they want to curb their risks of insider threats. Research indicates that threats from insiders are growing. Sometimes, the risks happen due to malice, such as if an employee wants to get revenge on a company for perceived wrongdoing. Issues can also arise due to employee mistakes, or if hackers take over workers’ accounts.
Zero trust challenges firms to assume no implicit level of trust, even from system administrators. This approach also means no single person could carry out a system change that affects its security. Zero trust functions on the idea that networks are always hostile. Companies often overlook how their employees could introduce risks. Zero trust minimizes those threats.
Some companies determine that if they don’t transition to zero trust security, they’ll get left behind as their peers make that move. A November 2019 report from Zscaler found that 59% of organizations plan to implement the zero-trust model in the next year, and 15% have already done so.
Companies including Kayak, Siemens and Google are using zero trust now, with Google being one of the early adopters of the option. Kayak’s system differentiates between devices owned by the brand and the gadgets owned by employees. It can also tell which devices on the network have out-of-date operating systems.
These well-known brands use zero trust for security, and the majority of organizations polled by Zscaler said they would soon. It’s time for companies to realize they may get viewed as out of touch for their old security practices unless they decide to change to the zero-trust model.
One of the principles of zero trust relates to least privilege. In other words, people only have the access they require to do their jobs. If a person takes a new role in a company, their access privileges change, too. Some firms reveal security shortcomings if their workers continue to have unnecessary access rights as they move throughout a company.
For example, a person might start in one department at a company and continue to have the access privileges associated with it even after they get transferred to a different part of the company and participate in wholly different work. The zero-trust model prevents that from happening and ensures that people have nothing more or less than the access required to complete their tasks.
Some previous versions of access control centered on things like an IP address — an aspect that someone could easily change with a virtual private network (VPN) tool. However, zero trust gets more specific when determining whether to grant access to someone. For example, it’ll examine who wants access to the data, what applications they want to access and when they want to use them.
If the system decides there are too many characteristics falling outside what’s expected, it won’t provide the access. Moreover, if the system finds ongoing patterns of strange behavior, such information may cause a company to start an internal investigation to see if someone’s trying to get any information they shouldn’t have.
The six reasons here illuminate some of the factors that cause companies to choose the zero-trust model. As the threat landscape becomes larger and more diverse, people should expect more companies to follow suit.
By Kayla Matthews






