The zero trust model is becoming more commonplace in security. It’s based on the realization that threats exist inside and outside of a network.
Limiting those requires verifying a person’s permission to access something during every request they make.
Zero Trust Computing is a security concept that operates on the premise “never trust, always verify.” Instead of assuming that everything inside an organization’s network can be trusted, it advocates for treating every access request as if it originates from an untrusted network, even if it comes from inside the organization’s own perimeter.
Here are the primary benefits of implementing a Zero Trust model:
In the past, the primary aim of security models was to fortify an organization’s outer boundaries. Once secured, everything within was deemed safe. Yet, the digital evolution experienced by numerous businesses means that these older strategies no longer hold water.
The rise of Internet of Things (IoT) devices, the increasing trend of employees working on the move, and a heightened dependence on third-party vendors have all amplified potential risks. It’s a misconception for firms to believe in completely threat-free zones. They need to recognize the urgent need for a revamped security strategy. Just as businesses have pivoted their practices in the digital age, they must understand that a contemporary security framework is indispensable.
One of the principle goals in traditional security models was to keep an organization’s perimeter secure. Then, a firm could feel confident that anything within it was safe. However, the digital transformations that many companies have gone through mean that the old way of doing things is no longer sufficient.
Things like Internet of Things (IoT) devices, employees working while traveling and a greater reliance on third-party providers can all make threats go up. Companies cannot assume that threat-free environments exist, and they must understand that it’s time for a new security approach. In the same ways that businesses have adjusted their operations due to digitization, they must realize that the shift necessitates an updated security model.
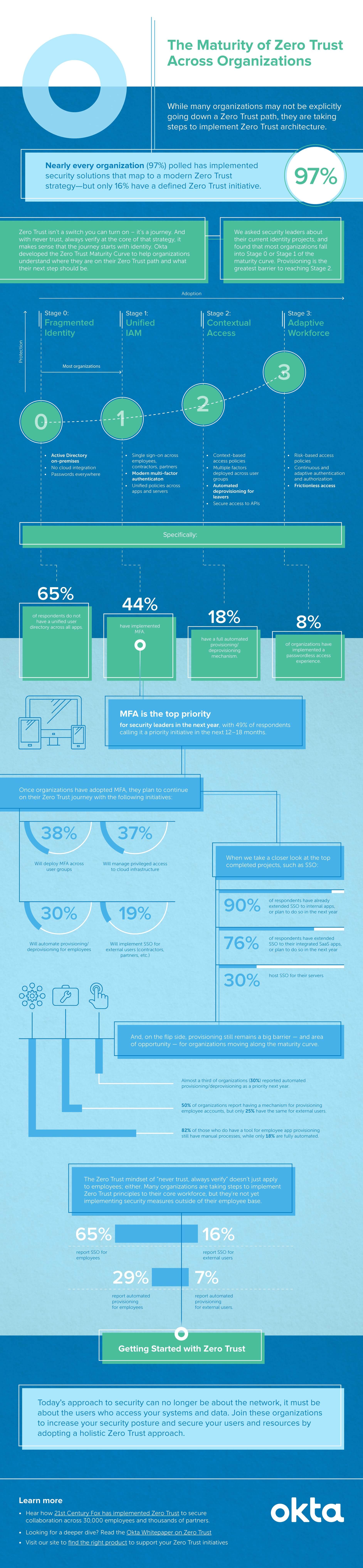
(Infographic Source: Okta)
Rather than anchoring security on an organization’s physical boundaries, the zero trust model prioritizes identity verification. This approach means that whether someone aims to retrieve data stored on-site or in the cloud, access is granted based on verified credentials, not location.
In the same vein, zero trust is relevant when accessing data from any device, eliminating the need for users to be in a specific locale to confirm their identity. This flexibility resonates with companies that frequently employ remote staff, considering the myriad of devices available for global data access.
With the ubiquity of mobile apps and handheld devices in our modern world, working from any location has never been easier. Zero trust ensures this flexibility does not compromise an organization’s security integrity.
One significant factor driving the surge in zero trust adoption among companies is the mounting concern over insider threats. Studies show that internal threats are on an upward trajectory. At times, this is fueled by disgruntled employees seeking retribution for perceived slights. However, unintentional mistakes by employees or cybercriminals gaining access to employee accounts can also be the culprits.
The essence of zero trust is not to grant inherent trust to anyone, not even to system administrators. With this model, no individual can single-handedly implement changes that compromise system security. Operating on the premise that all networks are potentially hostile, zero trust underscores the vulnerabilities that even employees can present. By adopting zero trust, businesses can substantially mitigate these internal risks.
Many firms recognize the risk of being outpaced by their competitors if they don’t adopt a zero trust security approach.
Notably, giants like Kayak, Siemens, and Google have incorporated zero trust into their security infrastructures. Google, in particular, was an early proponent of this approach. Kayak has a unique system that distinguishes between company-owned devices and those belonging to employees, even pinpointing devices running outdated software.
Companies need to be aware that sticking to dated security protocols might render them as outdated. Shifting to the zero-trust model is fast becoming the modern standard.
Central to the zero trust approach is the concept of ‘least privilege’. This means individuals are granted only the access necessary for their specific roles. As employees transition to new roles within a company, their access permissions should adjust accordingly. Some companies expose themselves to security risks when they allow employees to retain excessive access even as their positions change.
For instance, an employee may begin in one sector of a company and retain their initial access rights even after transitioning to a completely different role in another department. The zero trust framework eliminates this risk, ensuring that each individual possesses only the access needed for their current duties.
Earlier versions of access control largely depended on elements like IP addresses, which could be effortlessly altered using tools like virtual private networks (VPNs). In contrast, zero trust delves deeper when deciding if access should be granted. It evaluates factors such as the individual requesting access, the specific applications they aim to access, and the timing of their request.
If the system identifies numerous deviations from the norm, it denies access. Additionally, if there’s a consistent trend of unusual behavior, it could prompt the company to initiate an internal probe to determine any potential unauthorized data access attempts.
Adopting a Zero Trust model does come with its challenges, such as the initial complexity of setting it up, potential costs, and the need for continuous management and updating of policies. However, with the evolving threat landscape, the benefits it offers in enhancing organizational security are substantial.
By Gary Bernstein





