Updated: 11.19.2020
Infrastructure as a Service (IaaS) allows you to rent computing resources from a third party that you then access through the web. You essentially outsource having to set up or manage up racks, servers, storage, cooling equipment, power, or a physical place to house it all. You simply pay for only the computing capacity you need, and leave the dirty work of maintaining and securing the computer hardware to someone else, without incurring any upfront capital costs. See additional tips
It’s no secret many organizations rely on popular cloud providers like Amazon and Microsoft for access to computing infrastructure. The many perks of cloud services, such as the ability to quickly scale resources without the upfront cost of buying physical servers, have helped build a multibillion-dollar cloud industry that continues to grow each year.
Still, even though cloud has helped many companies, there are tradeoffs with cloud services such as Infrastructure-as-a-Service (IaaS) that organizations need to be aware of. With IaaS, a cloud provider maintains basic IT infrastructure such as servers, storage, and networks on your behalf, which is convenient but also raises concerns at the same time.
With On-Premises infrastructure, you have complete visibility and control over everything. You can physically see your infrastructure, and if something goes wrong, you have the power and ability to take immediate actions to fix issues.
But with cloud services, you need to trust your provider to properly secure your environment and respond to any security incidents in a timely manner, and as the data shows, many IT departments are hesitant to relinquish control and are afraid of outages or data loss that might occur in the cloud.
Adding to the worries, if a security incident occurs on cloud infrastructure, there’s sometimes confusion over who’s ultimately responsible for addressing the problem because there’s shared security responsibility between you and the provider. Who needs to take actions to remedy an issue depends on where in the stack the security incident actually occurred. Therefore, it’s critical for cloud users to know who’s responsible for what.
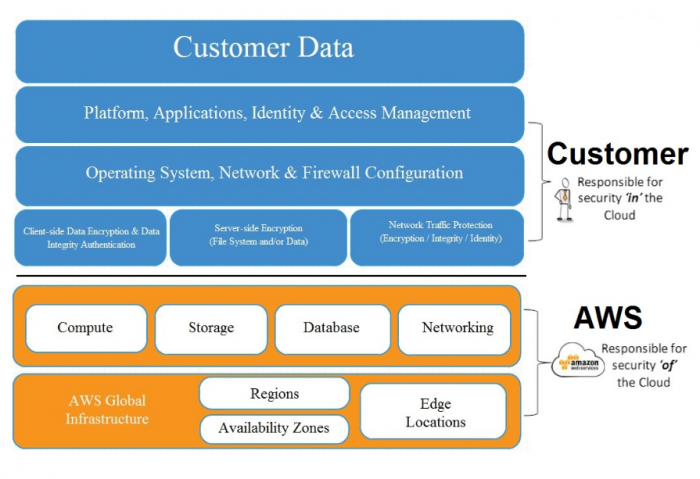
The two dominant cloud players, Amazon Web Services and Microsoft Azure, have both documented what they are responsible for as cloud providers when it comes to security. For example, in their shared responsibility model, Amazon Web Services has helpfully broken AWS security responsibilities into two main buckets:
“Security of the cloud” = everything the provider does, including:
“Security in the cloud” = everything you’re responsible for, including:
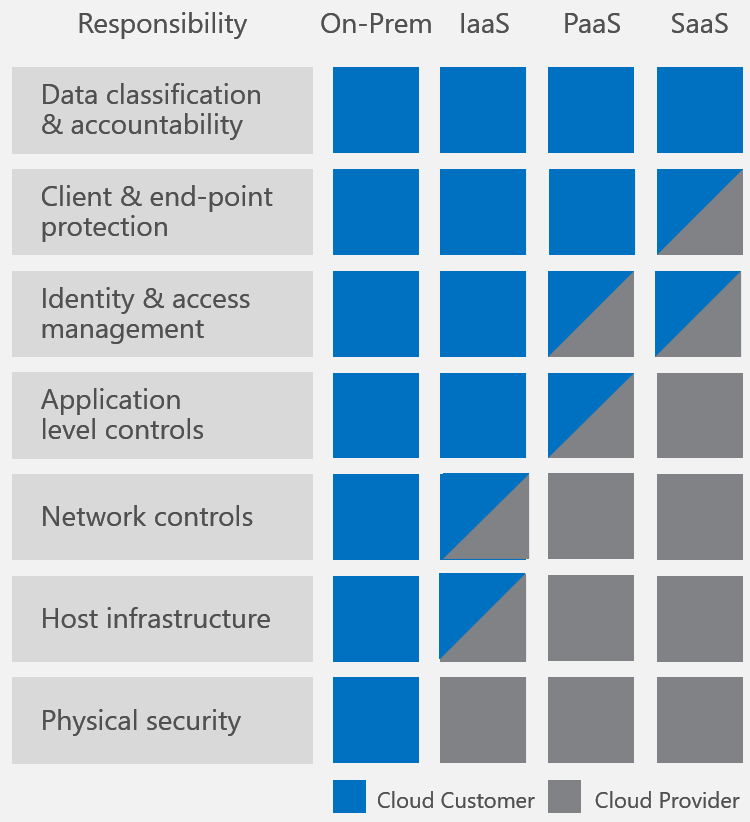
Microsoft also draws a clear line that separates what cloud Service Providers and cloud customers are responsible for. Their March 2016 document entitled Shared Responsibilities for Cloud Computing goes one step further by breaking down responsibility areas across different cloud models including IaaS, PaaS, and SaaS.
With all three service models, the cloud provider is solely responsible for physical security of infrastructure. And like with AWS all Azure users, regardless of what cloud model they take advantage of, are responsible for data classification and availability to make sure sensitive customer data is properly handled across all of the cloud models. But there are varying degrees of responsibility when it comes to end-point protection, identity & access management, application level controls, network controls, and host infrastructure. As a general rule of thumb, the more control over infrastructure you have, the more security responsibility you have as well, with IaaS providing the most control and responsibility, followed by PaaS, and then SaaS.
In summary, a first step towards securing cloud infrastructure and data is understanding what you’re responsible for so you can take appropriate action. The cloud providers try to make this very clear so you know what you’re getting into when you sign up for their services.
But just because the providers make some promises, you still need to be careful. Providers like Amazon Web services and Azure are not typically on the hook for data loss or a breach due to labor disputes, utility failures, natural disasters, orders of government, or acts of terrorism or war. They also include language in their service agreements that state you are still responsible for backing up and archiving your content in case of a disaster… so even when the cloud provider is on the hook for security, you still need a solid “plan B” just in case.
By Peter Tsai





