We’ve recently covered a few real time hacking maps but have decided to extend the list based on the recent ransomware activities with some additional real time hacking attack and ransomware tracking maps.
Ransomware refers to malicious software that blocks access to a computer system until a ransom is paid. Recent problems experienced with Ransomware are evident from infections, which have occurred in 99 countries including China and Russia. The organization that was worst hit by the attack was the National health Service in England. It was reported that there was a WannaCry programme that demanded a payment of $300 dollars paid in virtual currency Bitcoin for the files to be unlocked. The DDoS attack, which targeted the DNS service provider DYN led to approximately three hours of service outage. Various lessons can be learned following the threats that Ransomware present to organizations. Organizations should ensure adequate disaster preparation to neutralize dangers such as unique files being held hostage. Ransomware protection should also address the human element by ensuring expansive user training.
With live hacking and ransomware tracking maps, organizations can now identify hacking attempts or cyber-attacks from different parts of the world as they happen in real time.
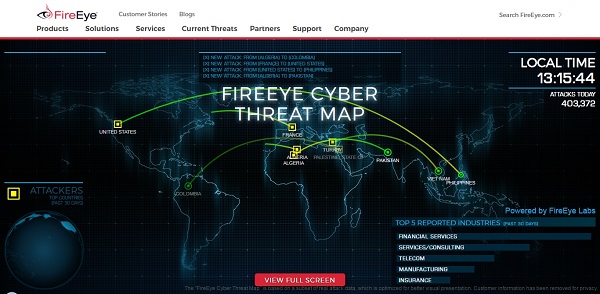
Real time visualization of global cyber attacks. Displays the total number of detected daily attacks as well as the five most attacked industries for the past 30 days. The service lists detected attacks in real time and shows attacking and target country.
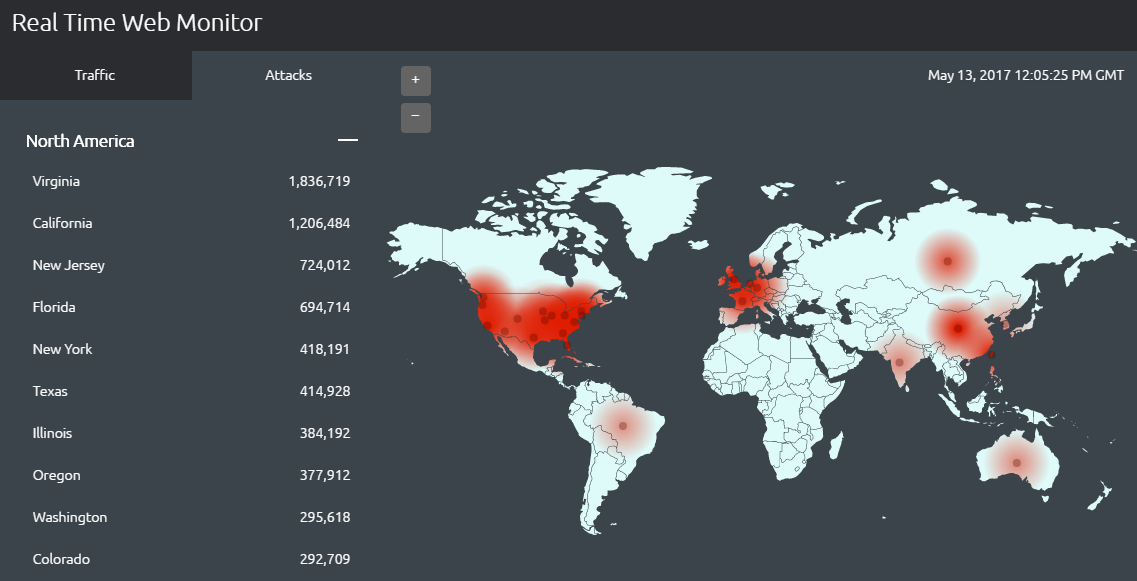
Akamai monitors internet conditions globally around the clock. With the real-time data, it becomes possible to identify some of the global regions that are targets of great web attack traffic.
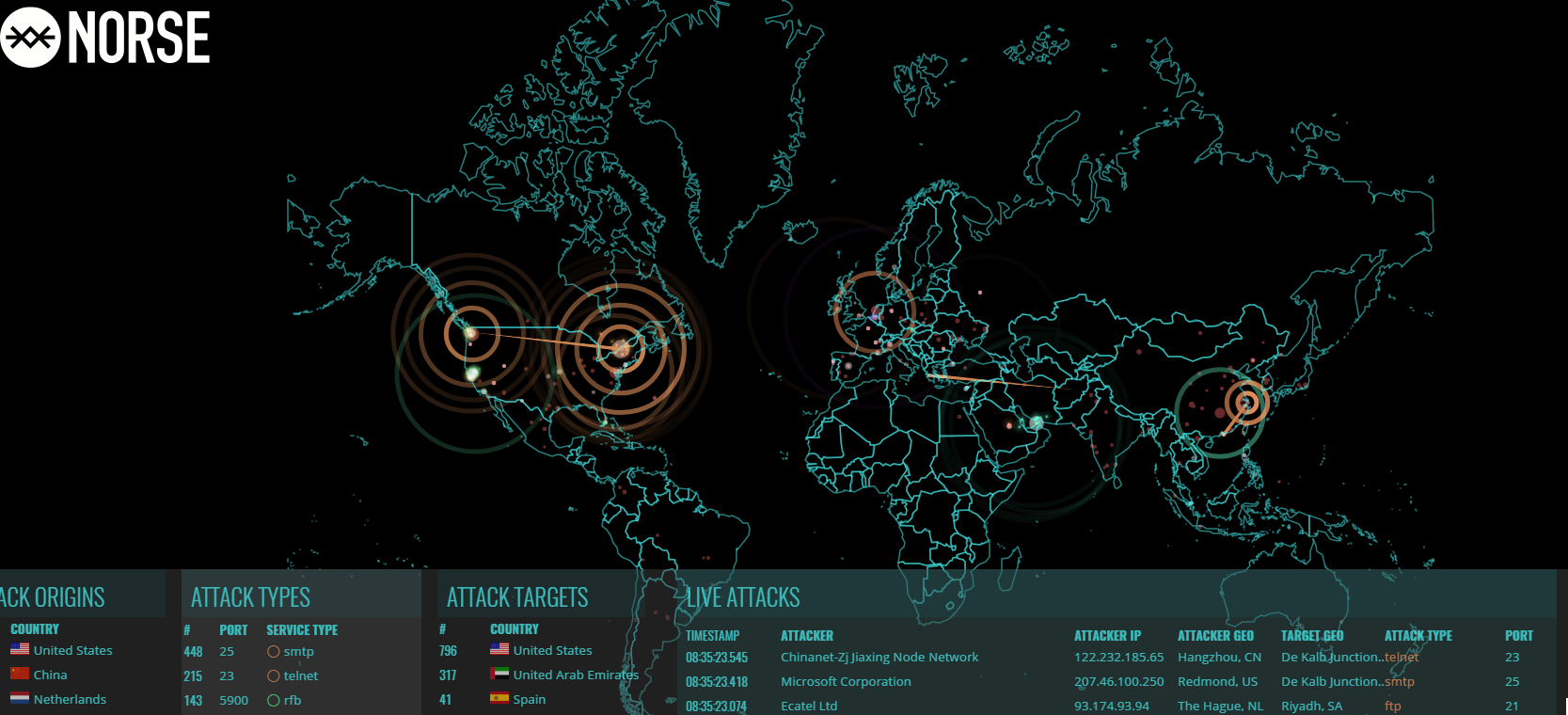
Norse presents proactive security solutions, which helps to defend organizations against the advanced threats in the current world following the global ‘dark intelligence’ platform. With cyber-attacks becoming increasingly sophisticated in the modern world, it is important for organizations to ensure they have solutions to avoid the interruption of operations.
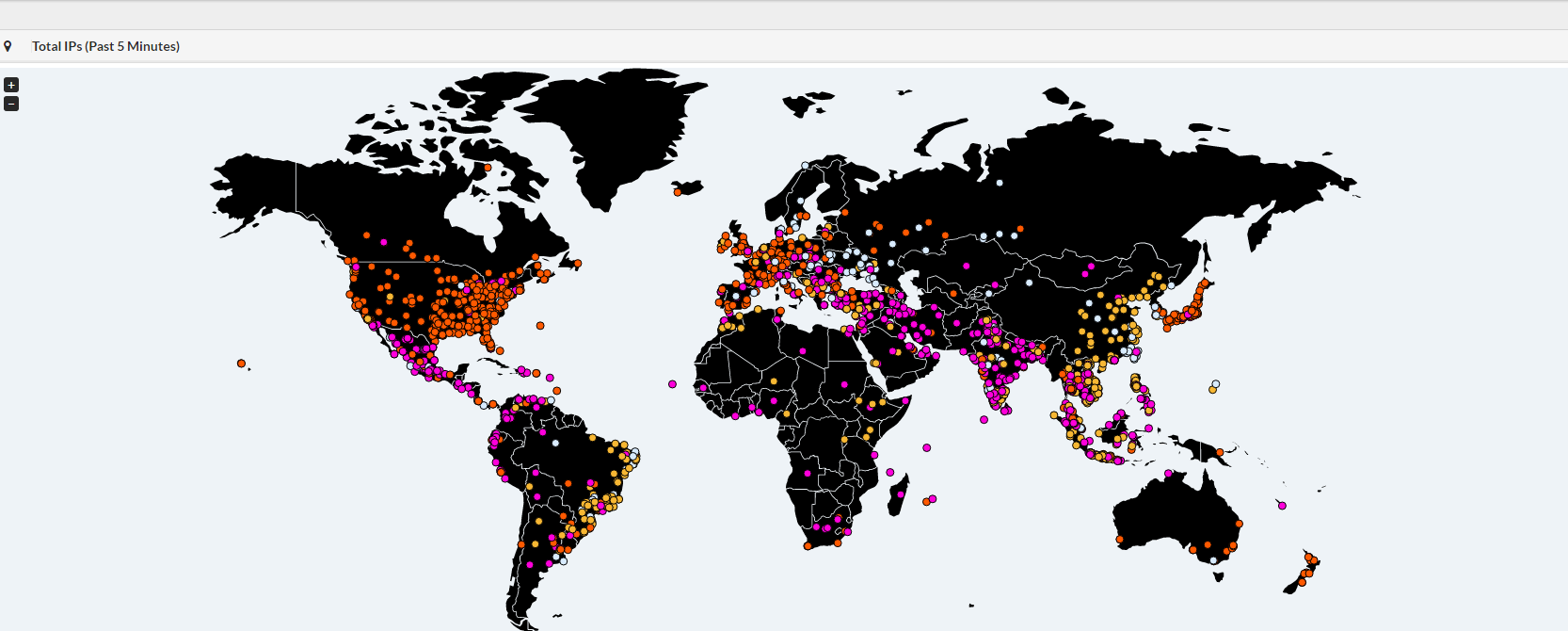
Intel Malwaretech enhances the visualization of maps that display geographical distribution of malware infection. It uses a live map that displays a blip whenever an infected computer pings the tracking servers.
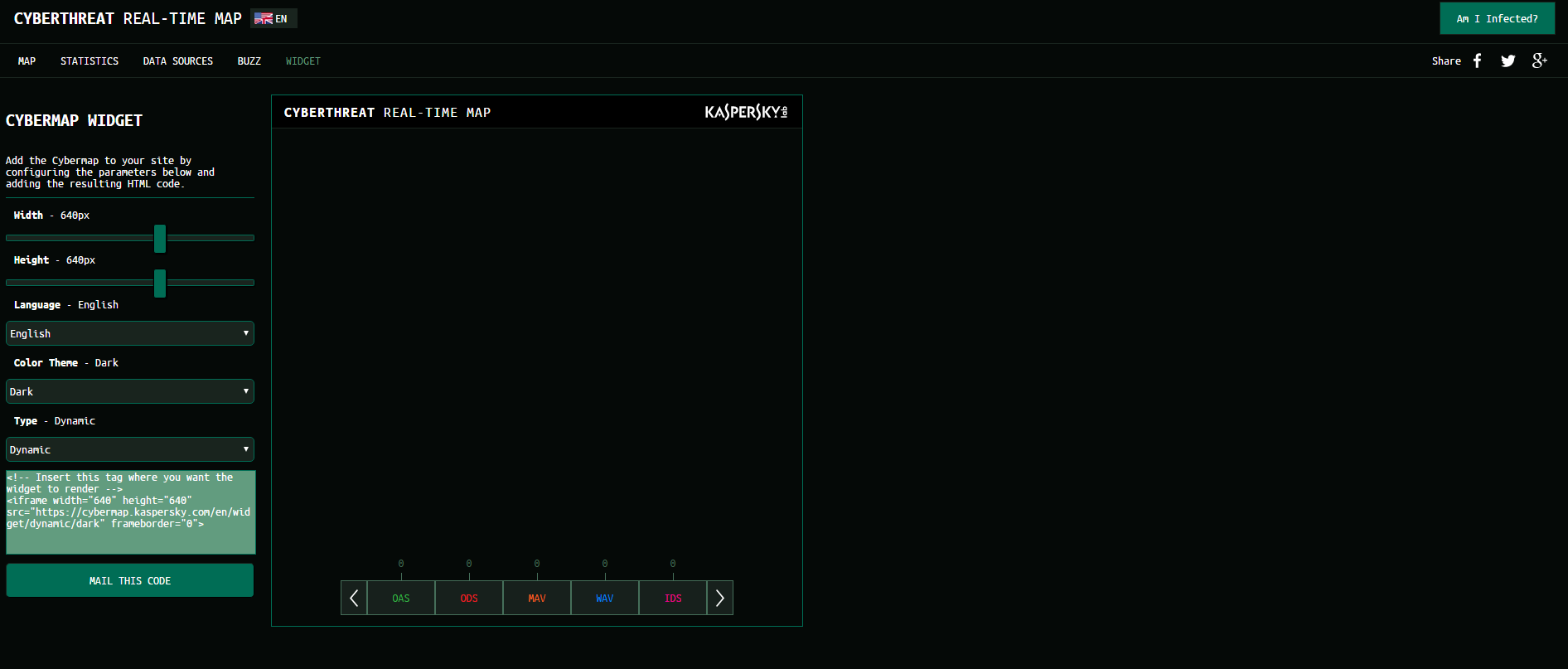
Malware detection flow visualization that uses Kaspersky data to show cyber threats discovered worldwide. It also displays botnet activity. Visitors can view cyber threat stats for a selected country.
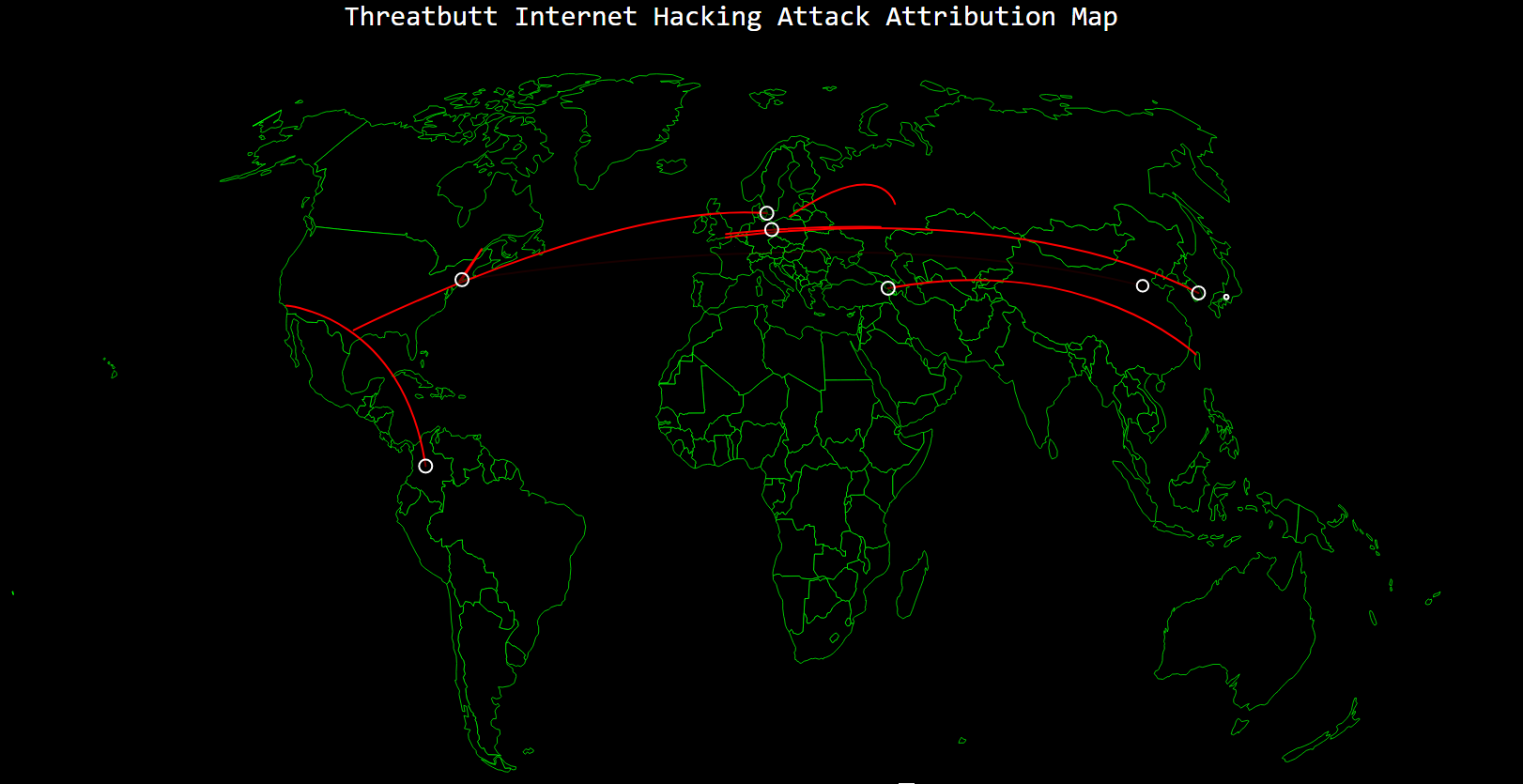
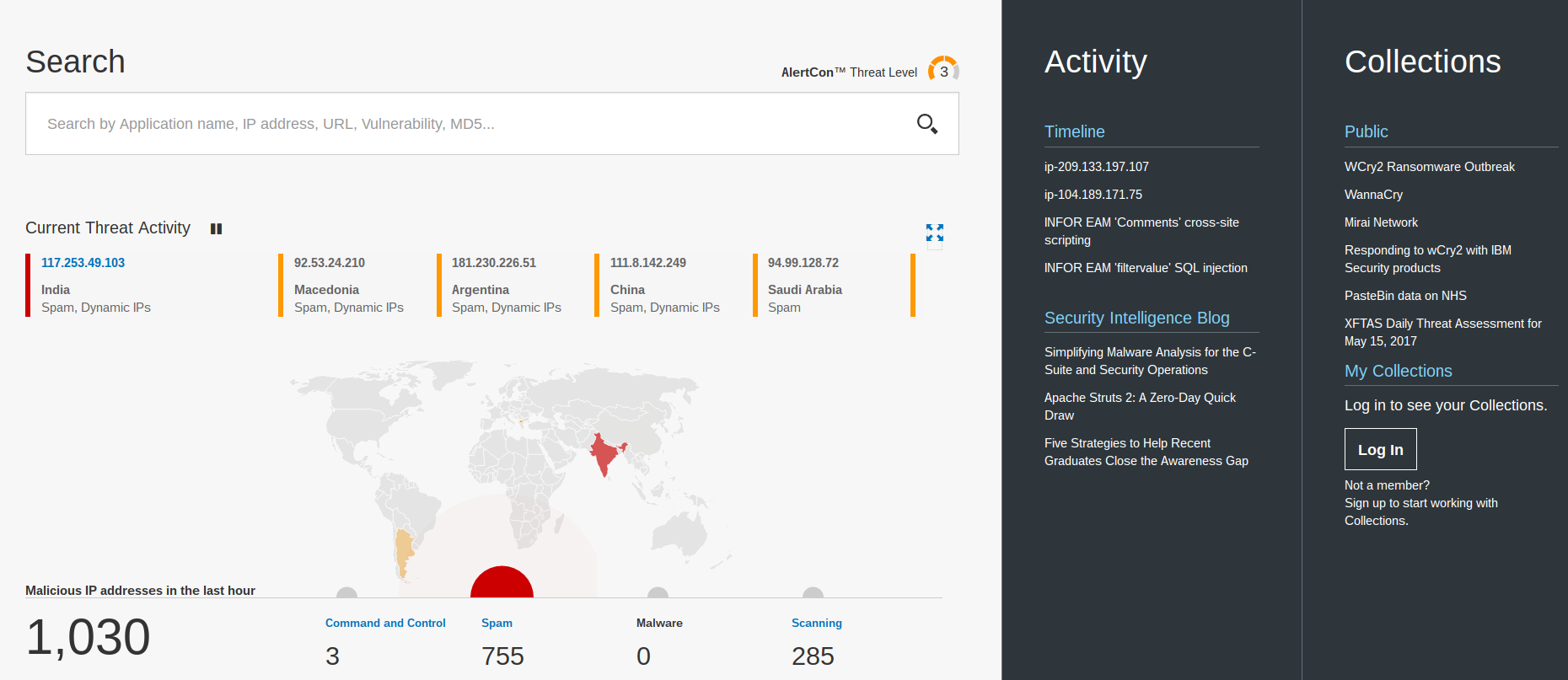
Shows detected global cyber attacks in real time. Visitors can view the attacking and the target IP addresses. The website displays the type of malware used, including unknown malware.
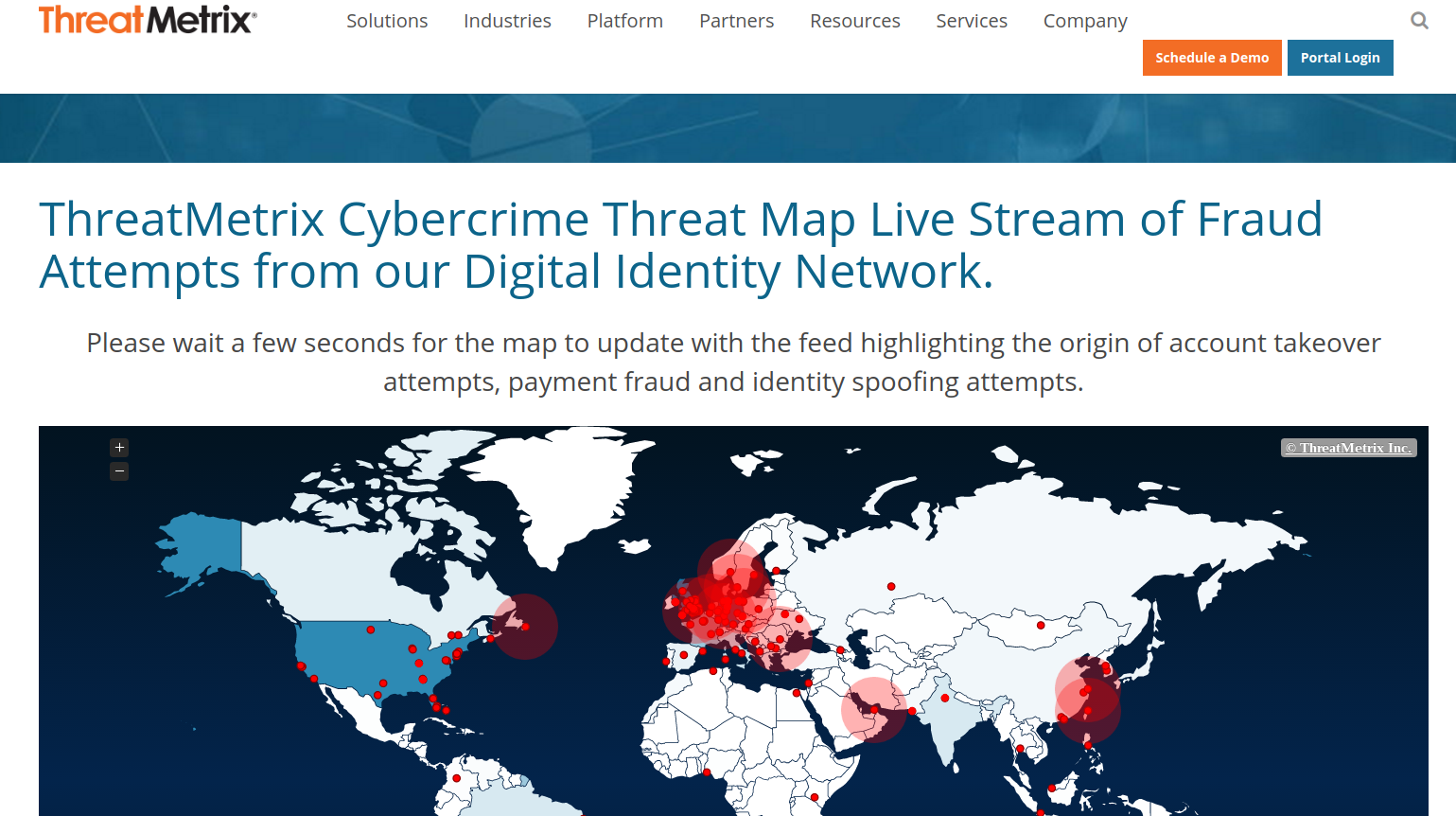
Threat Metrix provides a fairly unique fraud detection map. It offers a feed highlighting the origin of account takeover attempts, payment fraud and identity spoofing attempts around the world.
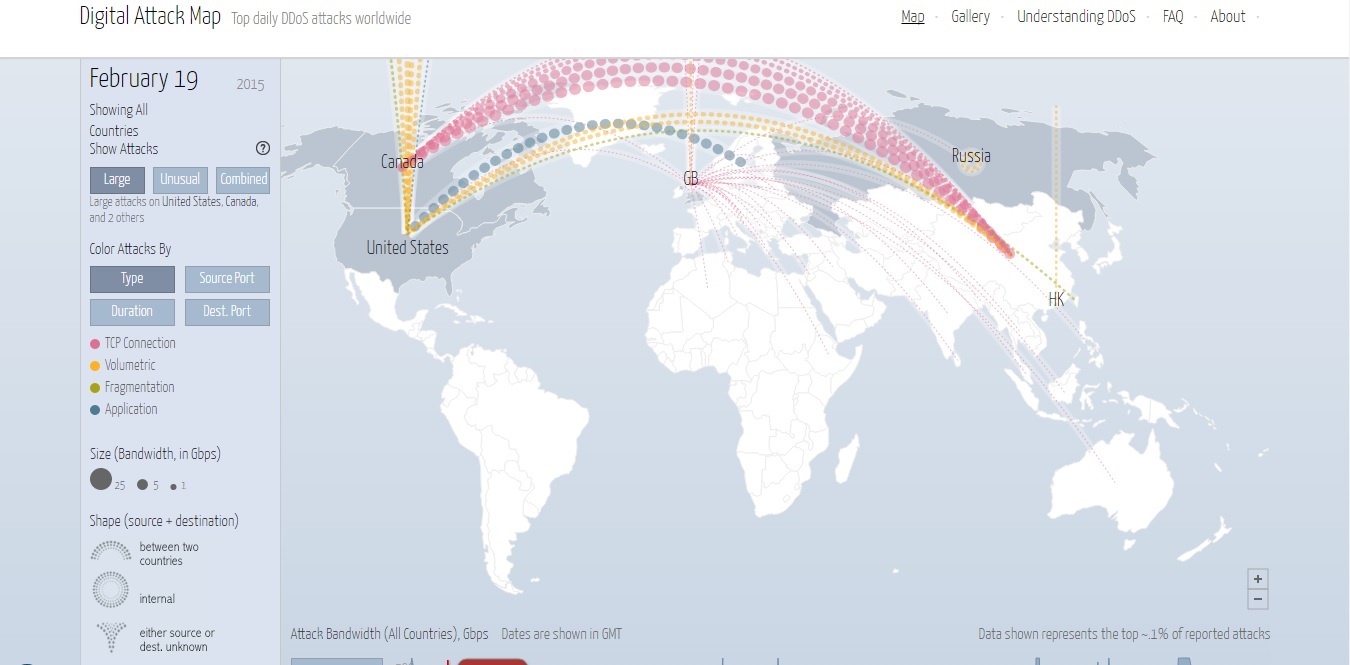
Displays daily statistics on the large and unusual DDoS attacks all over the world. Visitors can view which countries are experiencing unusual high traffic of cyber attacks for a given day and sort attacks by type, duration, source port, and destination port. Real time and pause mode.
Real time visualization of worldwide cyber attacks showing both the attacking and target country, as well as the malware used for the specific attack. The website also counts the total number of daily cyber attacks worldwide. Visitors can view which are the most attacked countries and where from these attacks originate.
By Kiril Kirilov